Note: This is a technical deep-dive into DearCry ransomware. If you want a preliminary analysis of the ransomware, you can find it here.
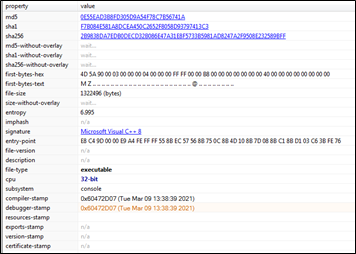
The Network Intelligence team initiated a Static analysis of the ransomware sample we received. The team used a tool called PEstudio, which helps in the static analysis of executable files.
Static Analysis
From the below screenshot, it is evident that the ransomware was compiled in C++ programming language. We can see the compiler timestamp, which indicates that the program was last compiled on Tuesday, March 9th, 2021, at 13:38:39. This timestamp coincides with the date on which DearCry ransomware first appeared.
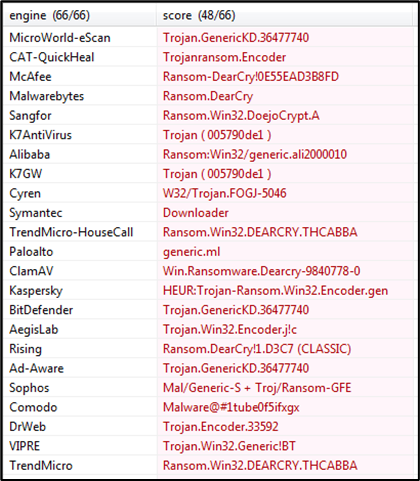
We then checked the Antivirus detection of the ransomware in the PEstudio tool on 16th March 2021. Most well-known antivirus engines detected the sample to be DearCry Ransomware.
The following screenshot depicts all the blacklisted system calls, DLL files that the ransomware used at the time of execution. One of the DLL files that stands out is crypt32.dll.
DearCry ransomware uses two encryption algorithms – AES-256 for encryption of files and RSA-2048 public key to encrypt the AES key. Here, we have used IDA tool, a multi-platform, multi-processor disassembler that translates machine-executable code into assembly language source code for debugging and reverse engineering.
During our analysis, we were able to get our hands on the RSA-2048 public key of the Threat actor. (See Figure 1)
 Figure 1 RSA-2048 Public Key
Figure 1 RSA-2048 Public Key
As we delved deeper into the malware, we found the list of file extensions that the ransomware will encrypt. (See Figure 2)
 Figure 2 List of file extensions
Figure 2 List of file extensions
We also found a Program Database (PDB) path during our analysis which most likely belongs to the threat actor’s system in which the ransomware was created. Here the PDB path points to a username John (See Figure 3)
 Figure 3 PDB Path
Figure 3 PDB Path
Upon execution, DearCry starts encrypting files with the extension defined in Figure (2) on the victim’s system using AES-256 and RSA-2048 encryption algorithms. It also modifies the file headers and prepends “DEARCRY!” string at the start of the file header. (See Figure 4)
 Figure 4 Encrypted File header
Figure 4 Encrypted File header
Post the encryption process, the encrypted files will have the “.CRYPT” extension appended to them. (See Figure 5)
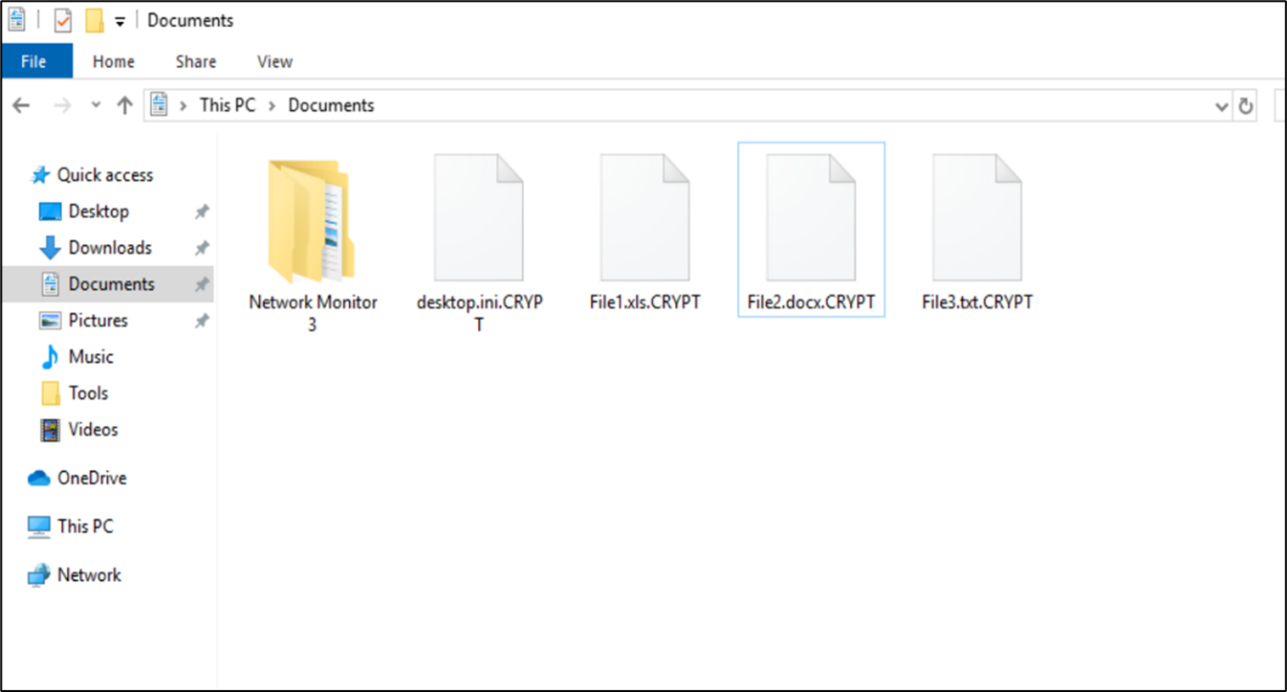 Figure 5 Encrypted files.
Figure 5 Encrypted files.
Post encryption of the files on the user system, the user is presented with a ransom note named “readme.txt,” which is saved on the victim’s desktop. The note contains two email addresses of the threat actor and a unique hash value. (See Figure 6). The victim will need to contact the Threat Actor (TA) by sending an email containing the hash values to the specified email address.
 Figure 6 Ransom Note
Figure 6 Ransom Note
DearCry / DoejoCrypt IOCs
During our analysis of the DearCry ransomware sample, the following IOCs were extracted.
Associated DearCry hashes
SHA256: 2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bffSHA256: e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6SHA256: feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33edeSHA256: FDEC933CA1DD1387D970EEEA32CE5D1F87940DFB6A403AB5FC149813726CBD65SHA256: 10BCE0FF6597F347C3CCA8363B7C81A8BFF52D2FF81245CD1E66A6E11AEB25DA
Associated DearCry file names
readme.txt
Associated DearCry emails
DearCry ransom note text
Your file has been encrypted!
If you want to decrypt, please contact us.
[email protected] or [email protected]
And please send me the following hash!
[victim id]
Conclusion
DearCry is reasonably simple ransomware leveraging the ProxyLogon vulnerabilities of Microsoft Exchange Servers. It is a typical example of how threat actors take advantage of newly disclosed vulnerabilities to make easy money.
As of this blog’s publishing date, there are no publicly known weaknesses of DearCry ransomware that can help victims get back their files. For decryption, paying the threat actors is the only option. Hence, prevention continues to be the best cure for this threat. Network Intelligence strongly recommends immediately updating all Microsoft Exchange Servers to the latest available patches released by Microsoft.
References
- The Network Intelligence team received a DearCry ransomware sample from https://bazaar.abuse.ch/
(Disclaimer: Kindly use the link for research purposes only and be careful while accessing the link. Network Intelligence is not responsible for any issues while or after accessing this link)
- https://www.winitor.com/ – PE Studio Tool
- https://www.hex-rays.com/products/ida/ – IDA tool
- https://en.wikipedia.org/wiki/C++
- https://docs.microsoft.com/en-us/windows/win32/seccrypto/crypt32-dll-versions
- https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
- https://en.wikipedia.org/wiki/RSA_(cryptosystem)
- https://en.wikipedia.org/wiki/Program_database
Mubbashir Shaikh is a cybersecurity analyst specializing in malicious emails and malware. He is passionate about Forensics and investigating cyber threats. When not analysing malicious alerts/emails, he enjoys videogames, cycling, and music.
1