Note: We have also done a technical analysis on DearCry. Read here.
It’s a warm summer morning. While sipping your morning coffee, you access the work email. But you’re unable to log in. After trying a few tricks you’ve read up in some tech blogs, you reach out to your IT team. They remote log-in to the server to investigate. All required services are running. There are no issues in CPU or RAM utilization. Nothing out of the ordinary.
During a random check of the downloads folder, they notice some weird extensions. Were these new files to be utilized on the server? Or files left over from a patch update?
By now, more people join the support staff who picked your call. You sense that there is something seriously wrong. But you don’t know what. “If only they told me something,” you tell yourself, although you know very well that despite their knowledge in the domain, even they seem to be clueless.
They finally start talking. What they have spotted has shaken them. You try to keep up, but in their nervousness, they forget that you may not be familiar with the technical jargon they use.
You spot words here and there. Words like “CRYPT,” “hash,” and “encryption.”
They say they’ve spotted a different file on your desktop containing a hash and a few email addresses.
You hear them asking each other,
“How could this happen?”
“The servers were encrypted.”
You drop the coffee mid-way and call your boss.
You and your boss have the same set of questions.
- How did the files get encrypted?
- Who did it?
- How did they get in?
- What to do now?
- How can we recover from this and get back to business as usual?
- What can be done to mitigate such attacks in the future?
How did the files get encrypted?
The answer is to the questions plaguing you is a rather simple and somewhat common term, Ransomware.
Simply put, Ransomware infects computer systems, encrypts files in those systems, and holds the user of systems to ransom. The user needs to pay the threat actors to get the system files decrypted. But paying the ransom is never a guarantee that you will get back your files.
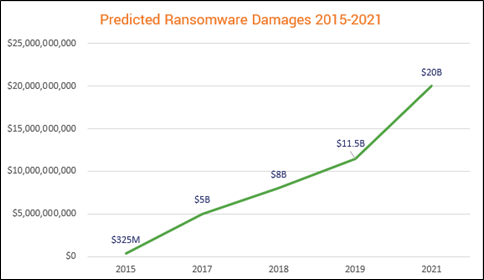
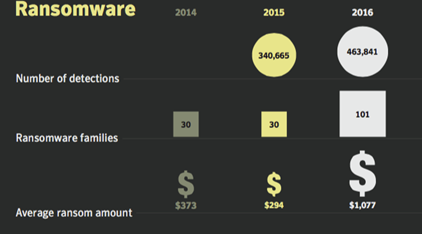
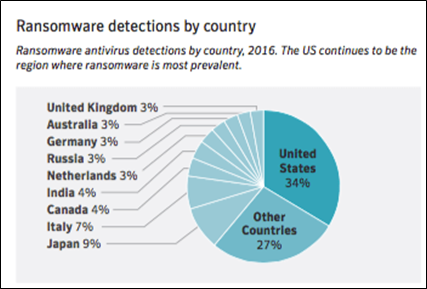
An attack on a corporate network that encrypts sensitive information can cost businesses millions of dollars. Ransomware attacks are getting complex and dangerous with each passing day. As per Symantec’s 2017 Internet Security Threat Report, “detections of ransomware increased by 36 per cent in 2016,” and it remains a dangerous threat facing both individuals and organizations. In contrast, the latest Threat Landscape Report 2020 by Bitdefender reveals that the total number of global ransomware reports increased by a whopping 715% in the first half of 2020 compared to the previous year. That’s an increase in percentage change by 20 times in just three years.
DearCry Ransomware
The exponential evolution in the number and complexity of Ransomware has led us to the latest version of this threat, which is wreaking havoc in the Cyberworld today, called “DearCry” or “Ransom:Win32/DoejoCrypt.A”
DearCry, like its name, shares similarities with the Wannacry Ransomware of 2017. But it is also different and more potent.
While Wannacry was mostly confined to attacking specific systems, current threat actors exploit ProxyLogon vulnerabilities and webshell to upload DearCry to Exchange servers, thereby encrypting the entire server’s contents.
DearCry’s encryption is based on a public-key cryptosystem. The public key is embedded inside the ransomware. This means that it doesn’t need to contact the attacker’s CnC server to encrypt your files. So even Exchange servers set up to only allow internet access for Exchange services can be encrypted. Nothing is possible without a decryption key that is in possession of the attacker.
Who are the threat actors behind DearCry?
On 2nd March 2021, Microsoft Threat Intelligence Center (MSTIC) revealed the attack by a state-sponsored threat actor identified by the name, Hafnium. They stated that Hafnium operated from China and was a highly skilled and sophisticated attacker.
In the past, Hafnium targeted entities in the United States for exfiltrating information from several industry sectors, including law firms, higher education institutions, defense contractors, infectious disease researchers, and NGOs. Hafnium is based in China but conducts operations from leased virtual private servers (VPS) in the United States.
How are the attacks orchestrated?
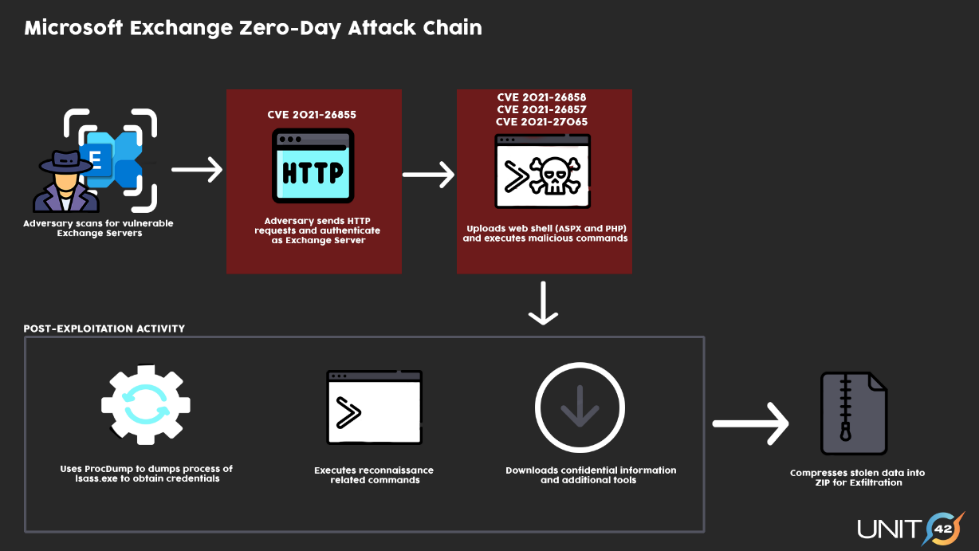
Microsoft revealed that threat actors compromised Microsoft Exchange servers using new zero-day ProxyLogon vulnerabilities (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065)Microsoft has since then released patches to fix those vulnerabilities. The threat actors exploit the vulnerabilities to gain access to the Exchange servers and then upload web shells. Post upload, the web shells are used to upload/download data and move laterally across the network.
In the case of DearCry Ransomware, the threat actor, instead of downloading sensitive data from Exchange servers, execute the ransomware on the server and encrypted vital files to demand a hefty ransom from organizations.
Start & Spread of DearCry Ransomware
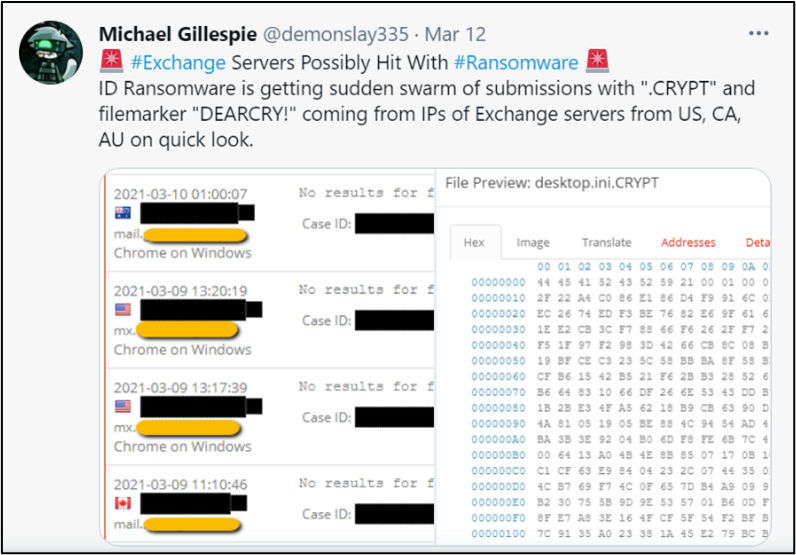
The earliest report on DearCry came on March 9th, from Michael Gillespie, the creator of a free ransomware identification service called ID Ransomware. He tweeted on Mar 12th that a new variant with “DEARCRY!” file markers was being submitted from Exchange servers into the ID Ransomware system.
Microsoft also confirmed that a new strain of ransomware targeting vulnerable on-premise Microsoft Exchange Server. They called it “DoejoCrypt.”
Michael Gillespie said that, as of March 11th, he had seen six unique IP addresses from the United States, Canada, and Australia attributed to DearCry reported into ID Ransomware.
MalwareHunterTeam, a security researcher collective associated with ID Ransomware, tweeted reports from victims in Austria and Denmark.
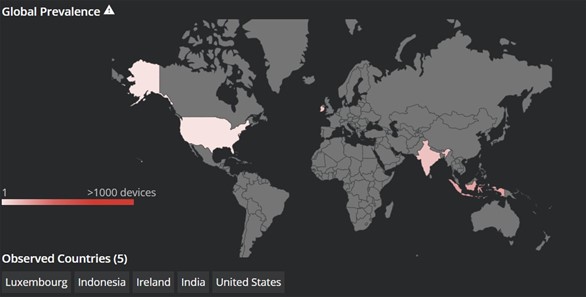
McAfee’s Head of Cyber Investigations, John Fokker, confirmed that there were victims in multiple countries, including United States, Luxembourg, Indonesia, Ireland, India, and Germany.
Mitigation for DearCry Ransomware
- Take preventive measures:
Like for every cyber-attack, prevention is the best cure for ransomware. Ransomware data breaches stem from the exploitation of known vulnerabilities (for example, in third-party software) or simple security failings (improper access controls, database misconfiguration, and default vendor accounts) rather than zero-days. Preventive security measures are far more efficient and effective in mitigating most cyber threats.
- Install Exchange Patches for ProxyLogon Vulnerability:
Microsoft has released patches to fix the ProxyLogon vulnerability in their Exchange servers (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065). Ensure all Exchange servers have installed the patches to plug the proxy logon vulnerability.
- One-Click Microsoft Exchange On-Premises Mitigation Tool:
By downloading and running this tool, which includes the latest Microsoft Safety Scanner, customers will automatically mitigate CVE-2021-26855 on any Exchange server on which it is deployed. This tool is not a replacement for the Exchange security update but is one of the fastest and easiest ways to mitigate risks to internet-connected, on-premise Exchange Servers.
- Backup your files:
One of the primary and crucial mitigation tactics that you can use against ransomware is taking a backup regularly of your files. Backup files should be stored in a separate system not attached to your network. In the event of a ransomware breach, backing up your files can allow you to restore information without paying the attacker.
- Patch your devices regularly:
The hackers can leverage any vulnerability to make a quick buck or launch a global attack like WannaCry Ransomware. The best solution to limit vulnerabilities is to patch systems regularly. Unfortunately, in many organizations, there are no systematic processes to track and install the latest patches. This leaves them highly vulnerable to attacks. Organizations should ensure all the systems and servers are up to date with the latest patches.
- Using Endpoint Security Solutions:
Gone are those days when you could just install a reasonably good Antivirus product and forget about cybersecurity. The cybercrime world is evolving at a pace at which antivirus programs cannot keep up. Organizations should invest in advanced Endpoint security solutions, preferably using Machine Learning and Artificial Intelligence to spot and remediate threats that traditional antiviruses miss.
- Training Employees:
Security awareness training is one of the most cost-effective ways to reduce your chance of suffering a ransomware attack. Training and educating employees on an ongoing basis is crucial. If employees know what to look for, they will be less likely to click on a suspicious email or attachment. Organizations can often prevent an attack before it even happens if the employees are suitably trained and aware. From an Information Security standpoint, it is far better never to download a malicious file than to hope that an antivirus program catches it.
- Regular Penetration Testing:
A penetration test, also known as a pen-test, is a simulated cyber-attack against your computer system to detect exploitable vulnerabilities. By conducting regular pen-tests, you can identify weaknesses before a malicious actor does. Regular pen-tests provide valuable lessons on your organization’s cybersecurity requirements and needs.
- Get Cyber Insurance:
No matter how secure your organization is, it can still be compromised with reconnaissance and resources. In such situations, Cyber insurance becomes relevant. Cyber insurance policies help in protecting against data breaches and other incidents. Purchasing a good-quality cyber insurance plan that covers instances of ransomware can save organizations significant amounts of money. While some policies cover ransom payments, others do not. Hence ask around and get multiple quotes before finalizing.
Remediation
The steps for remediation of the ProxyLogon vulnerabilities can be viewed here.
The remediation steps for DearCry Ransomware are given below.
- Disconnect from the network:
If a system is detected to be compromised by DearCry Ransomware, disconnect it from the network.
- Perform Log Analysis:
Performing log analysis of the Exchange logs will help understand where the web shells were uploaded to and ran from.
- Rebuild Server and Restore Backups:
Currently, there is no way to decrypt files encrypted by the DearCry ransomware. The Exchange servers will need to be rebuilt from scratch and the data restored from backups.
DearCry / DoejoCrypt IOCs
During our analysis of the DearCry ransomware sample, the following IOCs were extracted.
Associated DearCry SHA256 hashes:
- 2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bffS
- e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6SH
- feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33edeS
- FDEC933CA1DD1387D970EEEA32CE5D1F87940DFB6A403AB5FC149813726CBD65
- 10BCE0FF6597F347C3CCA8363B7C81A8BFF52D2FF81245CD1E66A6E11AEB25DA
Associated DearCry file names:
readme.txt
Associated DearCry emails:
[email protected]@memail.com
DearCry ransom note text:
Your file has been encrypted! If you want to decrypt, please contact [email protected] or [email protected] please send me the following hash![victim id]
We have done a detailed analysis on DearCry ransomware, you can read it here (Link to DearCry Analysis blog)
P.S: We have also done a technical analysis on DearCry. Read here.
References:
- https://www.zdnet.com/article/everything-you-need-to-know-about-microsoft-exchange-server-hack/
- https://searchsecurity.techtarget.com/news/252497747/DearCry-ransomware-impacting-Microsoft-Exchange-servers
- https://outpost24.com/blog/How-to-mitigate-Ransomware-attacks
- https://touchstonesecurity.com/mitigate-ransomware-attacks/
- https://thinksecurenet.com/5-steps-to-successful-ransomware-mitigation/
- https://www.infrascale.com/wp-content/uploads/pdf/Infrascale-Steps-to-Mitigate-Ransomware.pdf
- https://blog.emsisoft.com/en/36921/8-critical-steps-to-take-after-a-ransomware-attack-ransomware-response-guide-for-businesses/
- https://www.backblaze.com/blog/complete-guide-ransomware/
- https://www.redteamsecure.com/blog/ransomware-prevention-and-steps-to-take-if-youre-attacked
- https://securityaffairs.co/wordpress/115428/security/microsoft-exchange-emergency-update.html
- https://news.sophos.com/en-us/2021/03/12/dearcry-ransomware-what-it-is-and-how-to-stop-it/
- https://www.rsa.com/en-us/blog/2021-03/hafnium-attacks-microsoft-exchange-users
- https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
- https://blogs.microsoft.com/on-the-issues/2021/03/02/new-nation-state-cyberattacks/
- https://www.computerweekly.com/news/252497918/Unusual-DearCry-ransomware-uses-rare-approach-to-encryption
- https://in.pcmag.com/security/141463/ransomware-hackers-start-exploiting-microsoft-exchange-server-flaws
- https://unit42.paloaltonetworks.com/remediation-steps-for-the-microsoft-exchange-server-vulnerabilities/
- https://www.cfcunderwriting.com/media/3765/proxylogon-remediation-guidance-cfc-march-21.pdf
Mubbashir Shaikh is a cybersecurity analyst specializing in malicious emails and malware. He is passionate about Forensics and investigating cyber threats. When not analysing malicious alerts/emails, he enjoys videogames, cycling, and music.
1