Security Analytics Using ELK
Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. Both sessions were great experiences and allowed me to see [more]

Few months back, I had the opportunity to conduct two workshops at BSidesDelhi and CSI Mumbai on the above topic. Both sessions were great experiences and allowed me to see [more]
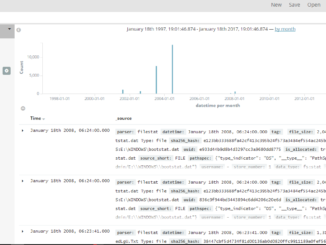
ELK Stack is a collection of three components – Elasticsearch, Logstash & Kibana Logstash – This component is responsible for processing incoming data. It takes input from different sources, [more]
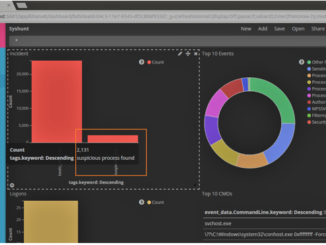
An important aspect of effective threat hunting is to understand what is normal in an environment. If a threat hunter is able to baseline the normal behaviour in a system [more]
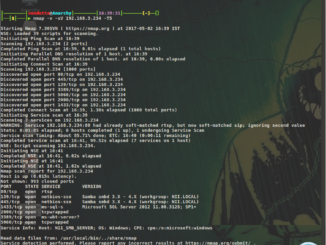
Before we start to configure our decoys and put it in our production environment, let’s take a look at what exactly it is and how it differs from the usual [more]
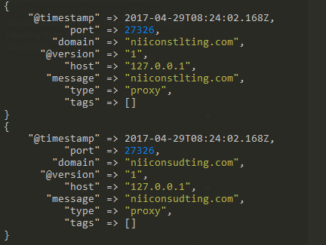
Most organizations face a barrage of attacks every day from threat actors around the globe. Among the various vectors, attackers have found relatively high degree of success by (spear) phishing [more]
If you are looking to navigate your way through the complexities of Big Data and its use in Security, here are some links to get you off the ground: Big [more]
Copyright © 2024 | WordPress Theme by MH Themes