
Trigger Warning – Abuse, Stalking, Death
She runs through an endless corridor of darkness, confused and helpless. Her heartbeat racing, her mind on overdrive. Why would he? How could he have known? How did he access her information? Her text messages, images, contact details, chats, places where she had visited, recordings of her phone calls – He had them all. What did he do? How? Just How??
The above may seem to be a horror story, but it indeed is real

Spying – Another bane of technology
It is an act of obtaining confidential information without the permission of the actual holder of the information. A person who does this is called a Spy. – Wikipedia
Spies have existed for hundreds of years. They have always used the latest available technologies to execute their tasks for stealing information. We have country-based spies, and in the current age, we have spies who steal company secrets on behalf of their competitors through technology.
With time, the act of using technology for spying has crept into homes, with one partner in a relationship spying on the other or abusers spying on their victims.
While spying on one’s partner is not necessarily a gender-based activity, in most of the cases reported, the victims are women. The perpetrators could be their male ex/current partner/co-worker/etc. Many of these women are victims of abuse too.
Abuse is a frequent companion to this form of spying. Because of this, many women are scared to report or seek help even when they are sure that they are being watched and tracked. They feel that reporting it to authorities would invoke the ire of their abuser and result in even more damage.
What is Stalkerware?
Stalkerware is any malicious program planted on the victim’s device with the objective of stalking. It is installed either by physically accessing the device or through social engineering. Recent Stalkerware applications are sold in a SAAS model. Once the application is installed on the device, it remains invisible. It continuously monitors the device depending on its functions like:

- Accessing contacts, galleries, messages.
- Recording calls
- Enabling front and back cameras for visual recording and/or audio recording through mics
- Recording what is typed onto the device and more.
Stalkerware works in invisible mode. The victim will not be able to see it in the list of installed applications. It may be disguised as one of the phone’s system-programs that come with the OS.
These applications usually are connected to their Command-and-Control server dashboard. This dashboard is where the stalker sees the data and interacts with the device to perform functions like enabling a microphone, starting cameras, etc.
Often, victims are known to the perpetrators, which means they would:
- Know personal details of the victim.
- Have access to the victim’s PC’s or cellular devices
- Have access to the victim’s online accounts.
This increases the potential damage that the perpetrator can cause using the information stolen through the stalkerware.

Below are a few cases where stalkerware was used to inflict harm on the victims.
- Lawyers prosecuting Luis Toledo discovered that he had installed stalkerware on his wife’s phone. This stalkerware was used to spy on her SMS messages. Luis was accused of murdering his wife and her children after spying on them for many days.

- Rasheeda Johnson Turner was arrested for hiring an assassin to kill her boyfriend and claim his life insurance policy. Enforcement officials discovered that she had installed stalkerware on her boyfriend’s phone, which kept the hitman informed about his movements.
- Brooks Owen Laughlin was accused of domestic violence and stalking his wife by tracking her movements using her iPhone’s Find My iPhone feature.
- Many women across the globe have complained about their ex-partners accessing intimate photographs/chats and other media from their mobile phone galleries using stalkerware and blackmailing them.
What many organizations legitimately use or promote as monitoring software can be misused as stalkerware. An abuser can misuse even software used for monitoring children to stalk his or her victims.
Below is a monitoring application. If you read through the about section, you can guess what it can be used for.

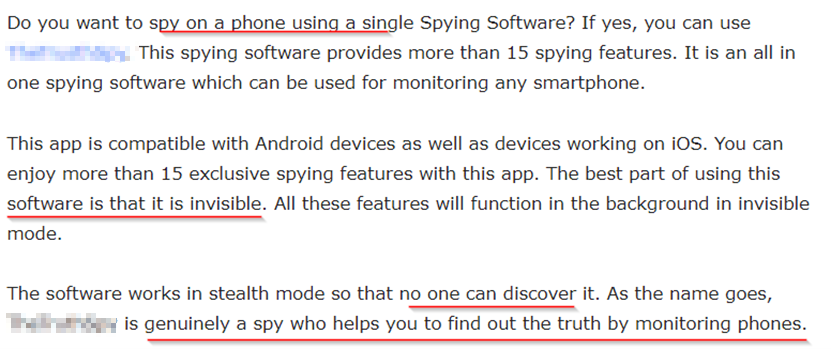
Statistics
Researchers in Canada published a Legal and Policy Analysis in 2019 titled Installing Fear. It explored various aspects involved in developing, using, and selling Smartphone Spyware and Stalkerware Applications. The report quotes various statistics on stalkerware related cases.
In 2014, the National Public Radio (NPR) surveyed 72 domestic violence shelters in the United States on cyberstalking and found that:
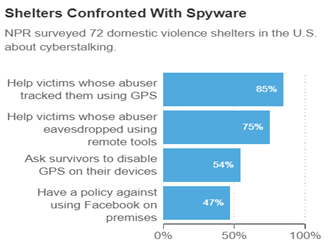
- 85% of shelters had “victims whose abusers tracked them using GPS,”
- 75% of shelters were had “victims whose abusers eavesdropped on their conversation remotely” — Using hidden mobile apps.
A 2012 survey of 750 victim-services agencies found that,
- 75% of domestic violence survivors are tracked through their cell phones or GPS devices
- 71% of domestic abusers monitor survivors’ computer activities
- 54% of abusers tracked survivors’ cell phones with stalking apps
A 2014 study sponsored by Digital Trust found that more than 50% of abusive partners used spyware or some other form of electronic surveillance to stalk victims.
As per NortonLifeLock Online Creeping Survey, 46 percent of Americans admit to ‘stalking’ an ex or current partner online by checking in on them without their knowledge or consent.
The growth in abuse through stalkerware prompted organizations like Avast, Avira, EFF (Electronic Frontier Foundation), Kaspersky to come together in 2019 to form the Coalition against stalkerware (CaS). CaS aims to facilitate communication between those organizations working to combat domestic violence and the security community for fighting stalking and harassment through stalkerware.

In a 2019 study by the CaS, it was observed that in the first eight months of 2019, 37,000+ users encountered stalkerware at least once. This was a 35% increase from the same period in 2018 when 27,500+ users were targeted.
Avast found that globally, there has been a 51% increase in the use of stalkerware since the lockdown in March until June 2020 in comparison to January and February 2020.
But there is scope for hope. Due to the efforts of organizations like Coalition against Stalkerware, more and more Anti-virus vendors are improving their engines to detect stalkerware faster.
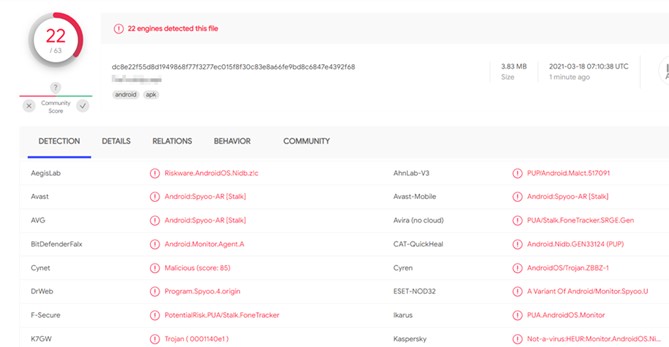
For instance, when we submitted the android installer of the monitoring application mentioned in the previous section to Virus Total, a platform for analyzing suspicious software, 22 out of 63 Antivirus vendors detected it as malicious.
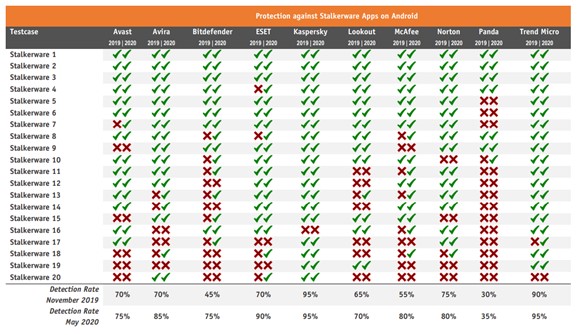
The below table is a comparison in detection rates of 20 Android Stalkerware applications over the last few months. You can see the spike in detection rate in May 2020 when compared to Nov 2019.
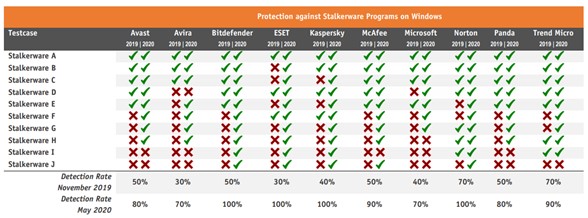
The below gives the same comparison for 10 Windows Stalkerware applications. Here the increase in detection rate is even more pronounced.
How Do You Protect Yourself?
While the technology to detect and neutralize stalkerware is catching up with the technology-based spying ecosystem, “prevention” continues to be the best cure for malice like stalkerware.
Following are a few steps for the prevention of abuse through stalkerware.

- Since stalkers are often known to victims, using personal relationships to access security information is the most common modus operandi used by them. So, do not divulge your passwords, security questions to anyone, including your friends, relatives, and acquaintances. This will prevent anyone from accessing your devices and online accounts.
- Ensure you change the passwords of your devices and accounts at regular intervals.
- Enforce 2FA – Two Factor authentication for your online accounts. Two-factor authentication works on the principle that a combination of “what you know” and “what you have” functions as the best deterrent. So if anyone attempts to access your account through your password (“what you know”), they will need an OTP (“what you have”) to proceed further.
- Keep track of applications installed on your devices. Do not install applications from untrusted, 3rd party sources.
- Install OS updates as soon as they are released. These updates will plug most vulnerabilities in your devices.
- Install a reliable Anti-virus software on your device capable enough to detect stalkerware.
- Do not accept cellular devices as gifts from untrusted sources – These may already have stalkerware installed on them.
How Do You Determine if Stalkerware is installed on your device by a suspect?
Ask yourself these questions:
- Does the suspect or anyone whom they could influence have access to your device and know its password?
- Is the suspect constantly bringing up targeted questions on topics only you are aware of?
- Does the suspect have a detailed idea of all your activities?
- Is the battery of your device draining quickly?
If you are feeling you are being spied upon, investigate further.
What to do if you suspect that stalkerware is installed on your phone
- Most often, stalking through applications is accompanied by some form of abuse. If you are a victim of domestic abuse, immediately seek help from trusted individuals and support groups.
- Put the mobile phone on airplane mode – This will disable the Bluetooth, data, and Wi-Fi connections.
- Change the passwords of all accounts linked to your mobile phone and enable Two Factor Authentication (2FA) for those accounts.
- Review the access privileges to your accounts and disable any unauthorized or suspicious permissions given.
- Reach out to local law enforcement authorities via another device. Stalking is a serious crime, and a case needs to be lodged with the authorities.
Technology, like any powerful tool, is a double-edged one. Stalkerware is the wrong edge of that tool. No matter the advances in cybersecurity and anti-virus technology, threat actors will continue to design more malicious and more complex stalkerware. While this cat and mouse game between malicious actors, abusers, and cybersecurity professionals plays out, the best way to secure oneself from being spied on is by being cautious and informed. Most of all, in the slightest hint of abuse or stalking, never hesitate to reach out to authorities and support groups whom you trust in.
We are the best anti-virus to protect ourselves.
References:
https://www.vice.com/en/topic/when-spies-come-home
Helping survivors of domestic abuse: What to do when you find stalkerware
Spyware user tracked boyfriend to have him killed by hitman
https://www.av-comparatives.org/wp content/uploads/2020/06/avc_stalkerware_2020.pdf
Photo Credits:
https://www.freepik.com/vectors/city City vector created by macrovector
https://www.freepik.com/vectors/infographic Infographic vector created by vectorjuice
https://www.freepik.com/vectors/background Background vector created by macrovector
https://www.freepik.com/photos/people People photo created by Dragana_Gordic
Experience of over a decade in the IT and CyberSecurity domain. A cyber-detective by nature,
and has solved numerous cyberattack-cases during his tenure at Network Intelligence. When not solving cybercrimes, he enjoys video-games and photography.
1