Clubhouse and its exponential growth during COVID-19
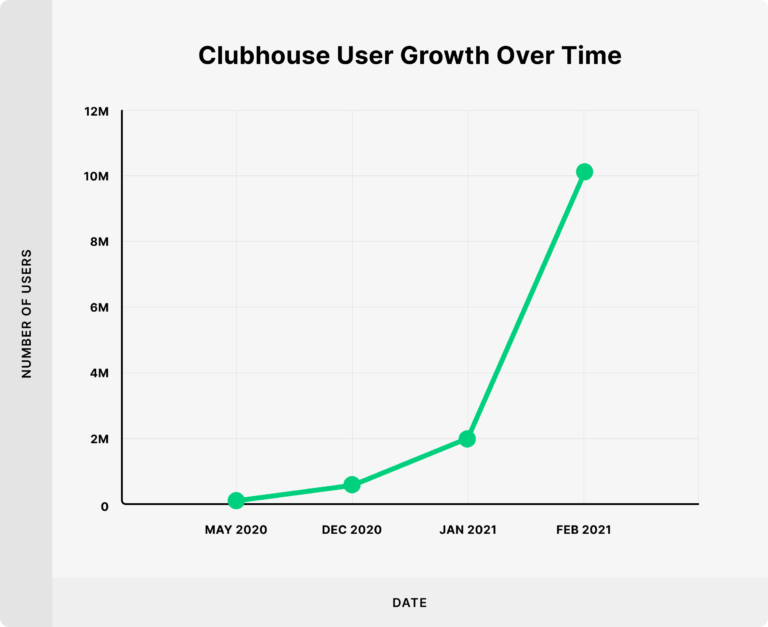
Clubhouse is an invite-only audio-chat iPhone app founded by Paul Davison and Rohan Seth. It allows users to create groups for conversations, including podcasts, audio conferences, etc. Launched in April 2020, the application became popular during the COVID-19 pandemic, reaching 600,000 registered users in December 2020, which exploded to 10 million weekly active users in Feb 2021. The app’s growth was accelerated by celebrities like Elon Musk inviting other celebrities for conversations on the platform. By January 2021, the company touched a valuation of USD 1 Billion. The popularity of the app is despite the fact that it is currently accessible only by invitation.
How was Clubhouse attacked?
One of the USPs of Clubhouse is the closed nature of the groups created by users. Only those with an invite to Clubhouse could listen in on the conversations of different groups. This USP was threatened when a developer in China published an open-source code to interact with the application without an invite and eavesdrop on conversations in the groups. Users were also able to stream the audio from multiple clubhouse rooms to their websites.
Another attacker was able to reverse engineer the code on a jailbroken iPhone to uncover the app’s source code and APIs. The re-engineered application then uses a bot-based system to interact with the backend and move through various Room-IDs of Clubhouse. Blocking the access to the bot would just result in another bot coming up in its place.

As per Stanford Internet Observatory (SIO), the backend of the application runs on the infrastructure maintained by Agora, a company based in Shanghai. Agora is an organisation that provides real-time engagement audio & video software. SIO found that private details like users’ IDs and chatroom IDs were being transferred over the network from the Clubhouse app to Agora in plaintext and not in an encrypted format. This is a severe vulnerability, which could be intercepted by hackers who would have access to unencrypted user-audio. SIO also noted that some user data was being sent to servers in China.
Other Privacy Concerns
The application requests access to not just the user’s data but also his/her contacts. It collects people’s personal information even before they engage with the app. This is a problematic design because a user cannot consent on behalf of others to allow Clubhouse to collect and use their personal information. Some experts have noted that Clubhouse could be creating shadow-profiles of these users.
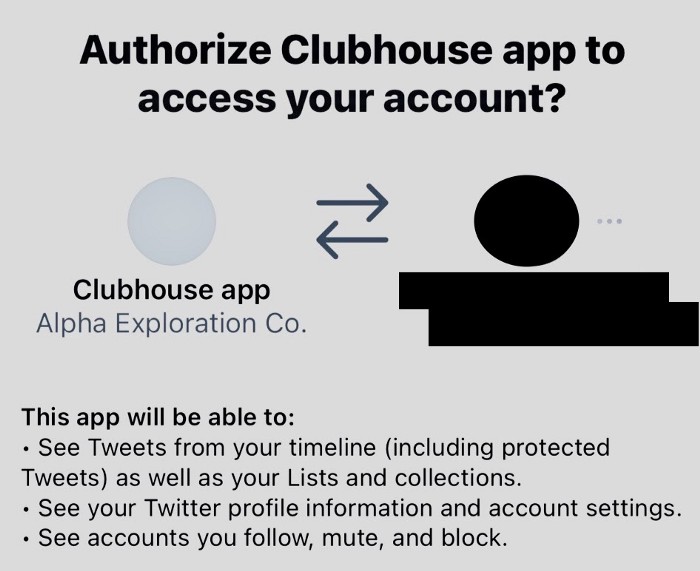
Clubhouse requests its users to connect with their Twitter accounts to find connections. The app states that it will be able to see tweets from the user’s timeline, see the user’s Twitter profile information, and the accounts that the user follows, mutes, or blocks. But Clubhouse doesn’t make it clear how this data will be used or why it needs it in the first place.
When it prompts the user to access the users’ contacts, it only gives a user selection of “Allow” and “Don’t Allow.” On selecting “Don’t Allow,” the application throws a pop up stating that it does need access to the user’s contacts.
Some experts have also expressed doubts regarding the app’s encryption of recordings.
Measures instituted by Clubhouse

As per Clubhouse, to tackle the recent breaches, the company will be engaging an external data security firm to review and validate their application and infrastructure.
At the same time, Agora has not yet commented on the security and privacy of the Clubhouse application. They have only stated that they do not store nor share personally identifiable information.
Ideally, in such cases, the application should take measures to reset the users’ accounts and passwords. The organisation should determine the extent of the breach and the loopholes through which the breach would have happened and remediate those loopholes. Post this, full breach-disclosure should be done to their users.
How impactful could such breaches be?
Hackers can exploit vulnerabilities of apps like Clubhouse, and the data of millions of users could be compromised. For instance, the teleconferencing platform Zoom, one of the largest such platforms globally, was the target of multiple attacks and vulnerabilities in 2020. The organisation disclosed two severe vulnerabilities, and it was discovered that it was possible for a user to bomb/join other meetings in the app.
After the attacks, five million Zoom credentials were available for purchase online. These included private data like the user’s login details and meeting room URLs.
How can such attacks be prevented?
The vulnerabilities in Clubhouse indicate a long-standing problem of insecure Software Development Lifecycle. Poor understanding of security and privacy issues at the design stage can lead to critical, baked-in vulnerabilities, which only increase in severity as the application’s usage increases.
Bugs in the application’s code can lead to vulnerabilities that can be easily exploited. Many developers do not look at applications from a security point of view. This results in poor security and privacy design. To prevent this, teams need to follow the Secure Software Development Life Cycle (SDLC). Following this framework enables developers and other stakeholders to ensure that security is implemented in the application code during the coding and testing phases. This framework can be tested using a source code review of the applications involved.
This leads to the broader need to move from a DevOps to a DevSecOps environment. In DevSecOps, everyone is accountable for security, and security actions and decisions are taken with the same scale, speed, and importance as application development and operations.
Additionally, regular Security Architecture Reviews would help in identifying such vulnerabilities and preventing breaches on time. Manual and/or automated Vulnerability Assessment and Penetration Testing (VAPT) will also help in the timely discovery of vulnerabilities in applications, servers, APIs, etc.
Lastly, proper end-to-end encryption measures to secure communication are critical for safeguarding customer data.
A perennial warning for Organisations

As the demand for data grows exponentially, so will the attempts to steal it. It is the responsibility of organisations to ensure that the applications they create are safe and secure right at the source code and design levels. Only by making security a strategic and cultural pillar can organisations achieve this difficult but critical objective. And this is the only way to protect their user’s data and sustain their trust even during exponential growth.
References
- https://telecom.economictimes.indiatimes.com/news/clubhouse-may-be-leaking-data-to-chinese-govt-stanford-report/80926229
- https://siliconangle.com/2021/02/22/clubhouse-suffers-data-breach-third-party-developer-designs-app-android-users/
- https://www.tomsguide.com/news/zoom-security-privacy-woes
- https://backlinko.com/clubhouse-users
Experience of over a decade in the IT and CyberSecurity domain. A cyber-detective by nature,
and has solved numerous cyberattack-cases during his tenure at Network Intelligence. When not solving cybercrimes, he enjoys video-games and photography.
3