The threat campaign is referred to as Operation Bleeding Bear. The attacks are currently limited to Ukrainian government agencies and businesses; however, the attack seems to have evolved and sophisticated over time, targeting almost all countries. The threat poses a risk to any government agency, non-profit or enterprise system. The malware campaign has been mapped to a threat group tracked as DEV-0586. Attack vectors employed by the hackers in this threat campaign include supply chain attack via IT infrastructure partners, exploitation of content management system OctoberCMS, and Log4j vulnerability. The malware execution is a 2-stage attack:
· In the first stage, the malware resides in the system mostly as stage1.exe, which upon execution, overwrites the MBR (master boot record) and displays a fake ransom note on victim systems.
· Once the stage 1 payload has gained a foothold, the stage 2 binary called stage2.exe acts as a downloader for a malicious file corrupter malware.
· Upon execution, the stage2.exe downloads and launches next-stage malware hosted on a Discord channel via a download link that is hardcoded in the downloader.
· This malicious file corrupter malware is further executed in memory via process hollowing to the InstallUtil process. The malware targets local hard drives, attached USB drives, mounted network shares, file matching internal hard-coded extension lists and corrupts them. The data-wiping malware deployed intends to corrupt data & cause Windows devices to become inoperable.
REMEDIATION
1. Block the threat indicators at their respective controls.
2. Ensure Microsoft Windows Workstations, Microsoft Exchange Server and Microsoft IIS Server are updated with the latest security patches.
3. Do not click on links or download untrusted email attachments coming from unknown email addresses.
4. Ensure Domain Accounts follows the least privilege principle and ensure Two-Factor authentication is enabled on all Business Email Accounts.
5. Ensure to enforce Two-Factor authentication for VPN clients, prior to connecting to Organization’s Resources through a VPN tunnel.
6. Ensure VPN client software and VPN servers are patched with the latest security updates released by the vendor.
7. Set PowerShell execution policy to execute only signed scripts. The change in policy on a system may be a way to detect malicious use of PowerShell.
8. Ensure Remote Desktop (RDP), Remote Procedure Call (RPC), and Virtual Network Computing (VNC) Services are strictly isolated from internet-facing cloud or on-premise IT infrastructure. And ensure these remote services are only allowed through VPN tunnels.
9. Educate employees about phishing attacks and use effective email filtering techniques from external sources.
10. Where possible, only permit the execution of signed scripts. Remove any unnecessary or unused shells or interpreters.
11. Use the SIGMA rule to detect WhisperGate destructive malware activity.
12. Use detection rules to identify WhisperGate malware activity on QRadar, Splunk, Kibana, Arcsight.
13. Enable Controlled Folder Access (CFA) in Microsoft Defender for Endpoint to prevent MBR/VBR modification.
14. Use application control configured to block execution of InstallUtil.exe if it is not required for a given system or network to prevent potential misuse by adversaries.
15. Ensure that unnecessary ports and services are closed to prevent the risk of discovery and potential exploitation.
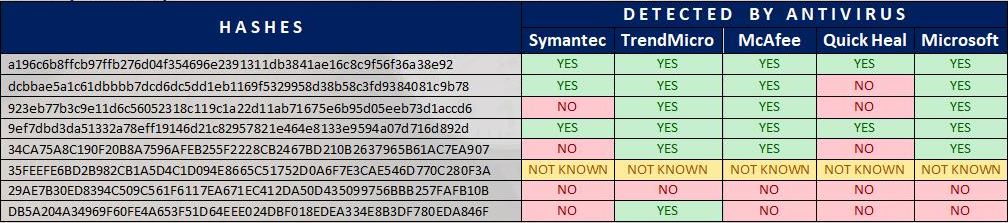
HASH (SHA-256)
URL
https[:]//cdn.discordapp[.]com/attachments/928503440139771947/930108637681184768/Tbopbh.jpg
REFERENCES
Destructive malware targeting Ukrainian organizations
Analysis of Destructive Malware (WhisperGate) targeting Ukraine
CISA urges US orgs to prepare for data-wiping cyberattacks
Nandeesha Basavaraj is a key member of the MDR Threat Intelligence team at Network Intelligence. He has experience in both SOC and Threat Intelligence. He is passionate about investigating cyber threats, threat actors’ motives, targets, attack behaviours and does threat hunting in his spare time. Apart from the work field, he enjoys playing cricket and badminton.