
An Overview of the most dreaded ransomware in recent times

Resurgence of Ransomware
In April 2019, the Cybereason Nocturnus team encountered several target machines infected with a ransomware called Sodinokibi, which spread via links to zip files containing malicious.
Sodinokibi (aka Sodin aka REvil) is installed on machines by exploiting an Oracle WebLogic vulnerability (CVE-2019-2725) and it propagates through exploit kits and spam.
In this blog, we explain present a technical analysis of the REvil ransomware, focusing on the delivery method and the defense mechanisms employed by the malware authors to evade anti-virus detection.
This malware is yet another sign of a resurgence of the ransomware threats, which we have been tracking for many years. The resurgence is corroborated by the fact that ransomware attack payments have doubled in the second quarter of this year.
In our analysis, we have observed interesting similarities between REvil and GrandCrab ransomware. Furthermore, reports by other security researchers also found similarities between the two ransomware. Interestingly, GrandCrab operators had claimed in June 2019 that they are retiring and discontinuing their operations.
How REvil works
REvil is typically deployed through human-operated ransomware campaigns, similar to Ryuk and WastedLocker. After breaking in, hackers use various tools and techniques to map the network, perform lateral movement, obtain domain administrator privileges, and deploy ransomware on all the computers to maximize the impact.
The initial access vectors can vary – from phishing emails with malicious attachments to compromised RDP (Remote Desktop Protocol) credentials and the exploitation of vulnerabilities in various public-facing services. Last year, REvil hackers gained access to systems by exploiting a known vulnerability in Oracle Weblogic (CVE-2019-2725).
According to Coveware’s report, REvil is distributed primarily through the following vectors:
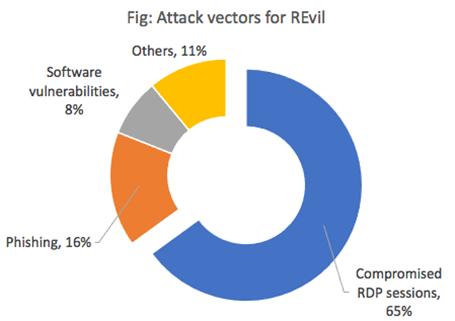
It is also believed that many REvil affiliates use brute force attacks to compromise RDP.
What happens during a REvil Attack
REvil stands apart from other ransomware programs by using Elliptic-curve Diffie-Hellman key exchange instead of RSA (Rivest-Shamir-Adleman) and Salsa20 instead of AES (Advanced Encryption Standard) to encrypt files. These cryptographic algorithms use shorter keys, are highly efficient, and are near impossible to crack if implemented correctly.
The initial infection vector used by the threat actor is a phishing email containing a malicious link. When accessed, the link downloads a malicious zip file. REvil/Sodinokibi zip files have a very low detection rate on VirusTotal, suggesting that most antivirus vendors do not flag the initial payload as malicious.
The zip file contains an obfuscated JavaScript file.
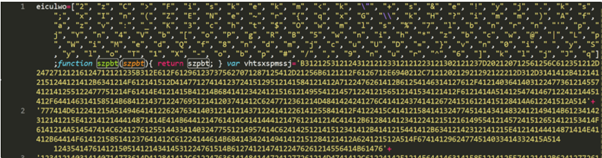
Fig: Obfuscated JavaScript file
When the user double clicks on the JavaScript file, WScript executes it.
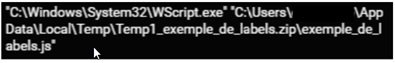
Fig: WScript executing malicious JavaScript
The JavaScript file de-obfuscates the PowerShell script and saves it in the temp directory.
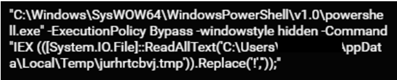
Next, the PowerShell script decodes an additional script that is Base64-encoded and executes it. The decoded script contains a .NET module also encoded with Base64, which is subsequently decoded and loaded into the PowerShell process memory.
REvil terminates processes like winword.exe, execel.exe, powerpt.exe, onenote.exe, wordpad.exe, outlook.exe, thunderbird.exe, firefox.exe, etc.
REvil also terminates services such as:
- Mepoc.exe – Belongs to product MailEnable Postoffice Connector Service developed by the company, MailEnable Pty Ltd. This file usually has the description, MailEnable Postoffice Connector Service.
- vssvc.exe – Manages and implements Volume Shadow Copies used for backup and other purposes. If this service is stopped, shadow copies will be unavailable for backup, and the backup may fail.
- memtas.exe – memta.exe is a process belonging to MailEnable from MailEnable Pty Ltd.
- veeam.exe – Veeam Endpoint Backup Software developed by Veeam Software AG software developer.
- SQL server related services
- viprePPLSvc.exe – viprePPLSvc.exe is a part of VIPRE and developed by VIPRE Security
- kavfsscs.exe – kavfsscs.exe is known as Kaspersky Anti-Virus for Windows Servers Enterprise Edition.
REvil encrypts all files on local drives except those listed in its configuration file.
Ransom Request
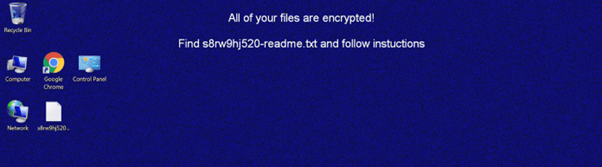
New wallpaper after ransomware encrypts the file
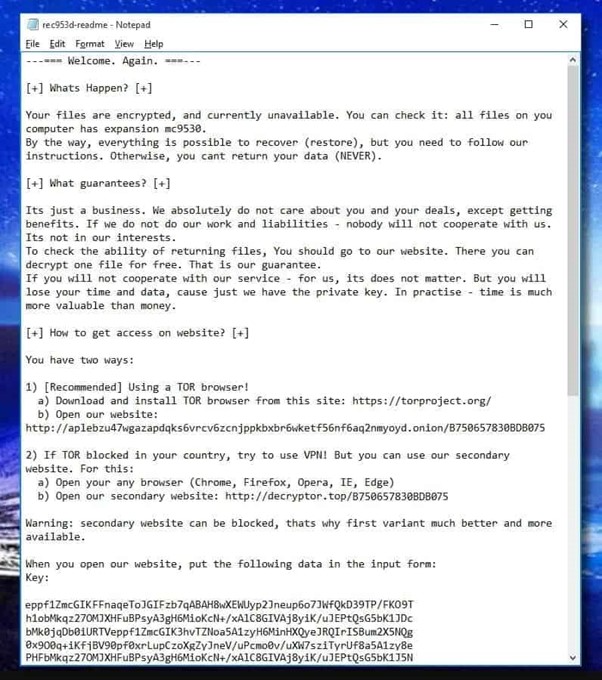
The ransom note for the ransomware
How to mitigate/defend against REvil
One of the signals of intrusion by REvil Sodinokibi is to detect the presence of terminals configured in different languages like those mentioned in the below table.
| Azerbaijani Latin | Georgian | Tartar | Romanian |
| Azeri | Kazakh | Kyrgyzstan | Turkmen |
| Uzbek | Ukrainian | Russian | Belarusian |
| Tajik | Armenian | Syriac | Syrian Arab |
If such an attack occurs, the organization needs to conduct a digital investigation activity through an Incident Response Team to identify payload and malicious artifacts within the corporate network.
Organizations should always secure their remote access with strong credentials and two-factor authentication. They should consider making such services available over VPN only. All publicly exposed servers, applications, and appliances should be regularly updated and scanned for vulnerabilities, misconfiguration, and suspicious behavior. Brute force protection that blocks excessive login attempts with the wrong credentials should also be enabled wherever possible.
Action Steps
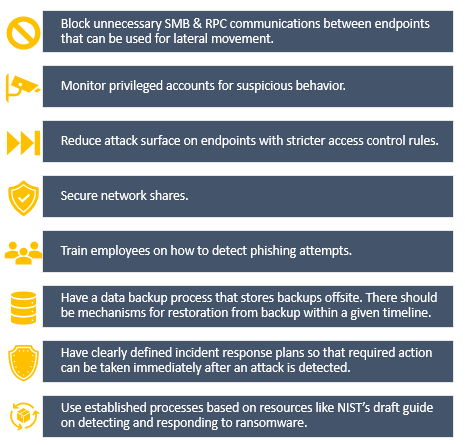
Following actions are required inside local networks to defend against the attack.
An Evolving Threat
Since April 2019, the REvil/Sodinokibi ransomware has become prolific and evolved into the world’s most widespread and destructive ransomware. It has since gone through several minor updates, and we assess that its industrious authors will continue to develop the ransomware, adding more features and improving its evasive capabilities.

References
https://www.cybereason.com/blog/the-sodinokibi-ransomware-attack
https://www.malwarebytes.com/ryuk-ransomware/
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
Nilesh is a cybersecurity expert specializing in malicious emails and malware. Nilesh has nine years of experience in malware analysis with different Anti-Virus vendors with a passion for investigating cyber threats and analyzing new malwares. When not tinkering with malwares, Nilesh enjoys cycling, Sci-Fi movies, fishkeeping, and gardening.