
Securing and Auditing Remote Process Automation
Securing and Auditing Remote Process Automation
1. Securing RPA:
RPA introduces a new attack surface that can be leveraged to disclose, steal, destroy or modify sensitive data and/or high-value information, access unauthorized applications and systems, and exploit vulnerabilities to gain further access to an organization. This section focusses on RPA cyber risks, leaving specific considerations about cognitive learning to be covered at another time.
1.1 Cyber risk Scenario
Abuse of privileged access
- An attacker compromises a highly privileged robotic user account used by some bots to gain access to sensitive data and move laterally within a network.
- An insider manipulate bot to destroy data, interrupting business processes.
Disclosure of sensitive data
- Mistakenly disclosure and upload of credit card information to a database accessible via the web by application creator
- An attacker using bot to leverages a generic account to steal sensitive data like intellectual property, leaving it difficult to identify true source of the leak
Security vulnerabilities
- An unknown vulnerability in robotics software allowing attackers remote access to an organization’s network.
- A bot creator upskills a bot to handle sensitive user data but does not secure the transmission of that data to/from the cloud.
Denial of service
- A bot is scheduled to execute in rapid sequence resulting in exhausting all available system resources and halting all bot activities.
- Bot controller is disrupted due to unplanned network, service or system outage resulting in loss of productivity, not easily replaced with human labour.
1.2 Securing RPA ecosystem:
While securing RPA implementations, an organization should consider the technical, process and human elements of the entire robotics system. A secure design should include the monitor product life cycle from requirements, selection, architecture, implementation and improvement operations. To build trust within a robotics platform, we should consider the approach provided below:
- Integrity: Whether we can trust that the data and results we get from bots have not been modified or altered?
- Traceability: Are we able to monitor and track bot activities to identify the misuse of robotics affecting confidentially, integrity or availability of other systems/data?
- Confidentiality: Can we protect sensitive data from being purposely or accidentally disclosed by bot creators and runners?
- Control: Are we controlling access and protecting privileged accounts leveraged by the robotics system and users?
1.3 Control & Robotic details:
Governance
- Establish a governance and management framework and establish roles and responsibilities for securing robotics operation
- Build strategy and security requirements for RPA within policies and monitor compliance with security policies related to RPA
- Manage RPA risks identified through a formal risk management program and increase awareness among bot creators and business users around the risks of RPA
Software and product security
- Perform risk analysis w. r. t. security architecture of RPA solutions, including bot creation, control and running. Identify security architecture flaws in product for connections across various environments, usage of virtualization methodologies, and authorization issues
- Conduct secure design review, including data flow analysis to verify that controls around security are integrated into the bot authentication, authorization and input validation
- Integrate security scanning tools as part of the bot creation process to scan code created in the back end for security vulnerabilities
- Scan bot created for security vulnerabilities using dynamic testing or security fuzzing technology to determine security flaws
- Ensure security controls in bot deployment
Digital identity and access
- Improve auditability (every step could be logged) and control over error-prone manual activities that elevate risk and noncompliance
- Manage user access privileges/segregation of duties risk; for example, use of a specialized security matrix authorizes bots to only perform the tasks assigned to them
- Implement security controls to protect credentials during robotic session run-time; for example, use of single sign-on (SSO) with lightweight directory access protocol (LDAP) supports secured logon to RPA interface
- Enforce passwords management across robotic sessions and centralize robotic identity and access management process; Incorporate encrypted credential managers to prevent leakage of secure authentication data.
Data identification and protection
- Perform compliance review to data regulations for the use of robotics and automation within an organization
- Monitoring and reviewing of sensitive data processed by robotics/automation to validate compliance with usage policies
- Integrity checking of robotics and automation code
Security operations
- Gather log data from controller and bot runners to provide an audit trail of activities, monitoring for abnormal spikes in the activity, access of systems and use of privileged accounts
- Conduct vulnerability assessment of your robotics application/platform and execute threat modelling of robotics sessions to determine technical loopholes or process gaps.
2. Robotic automation and orchestration to improve security
Many chief information officers (CIOs), chief information security officers (CISOs) and chief digital officers (CDOs) are challenged by legacy technologies and applications that do not work well with one another. This leaves their people manually gathering data from multiple systems, copying information from one system to another and switching between far too many applications to complete a single task.
To mitigate this issue, robotic capabilities is becoming more popular in the cybersecurity domain. Organizations are using robotics to:
- Reduce time to detect, analyze and respond to incidents, contributing to minimize risk exposure to an attack
- Reduce talent gap by automating resource-intensive tasks, helping organizations to manage operating expenses
- Minimize employee turnover due to lack of challenge or career progression by allowing employees to focus on higher-value tasks
- Automatically deploy and implement security controls when vulnerabilities or compliance exceptions are identified
- Make intelligent decisions quickly, resulting in high-quality and consistent outcomes
3. Auditing Bot/RPA:
Considerations at different phases of the audit when auditing a BOT environment.
- Planning:
- Detailed understanding of the areas where RPA is implemented
- Audit Plans
- Considerations:
- Audit plans and risk assessment for RPA
- Update to control matrices for automation through RPA
- Upfront involvement of IS Auditor/BOT Specialists
- Walkthrough
- Understanding of the process & IT
- Identification of Risks
- Identification of Controls
- Consideration:
- New IS/IT risks and scoped in systems
- Changes to automated controls, IPE/IUC, audit logs and interfaces
- More IS Risks and therefore enhanced ITGCC controls
- Design Evaluation:
- Evaluation of the Design of controls
- Exception handling process
- Identification of gaps
- Consideration:
- Substantial work by IS Auditor to test controls from Design (Configuration controls, logs, Cyber risks)
- Testing for IPE/IUC
- Operating
Effectiveness:
- Controls Testing
- Substantive Testing
- Consideration:
- Increased controls testing and minimal substantive testing
- Process governance and roles
- Reporting:
- Gaps reporting
- Recommendations
- Consideration:
- Logs and audit trails
- • Changes to control design, CM, SOPs, roles etc.
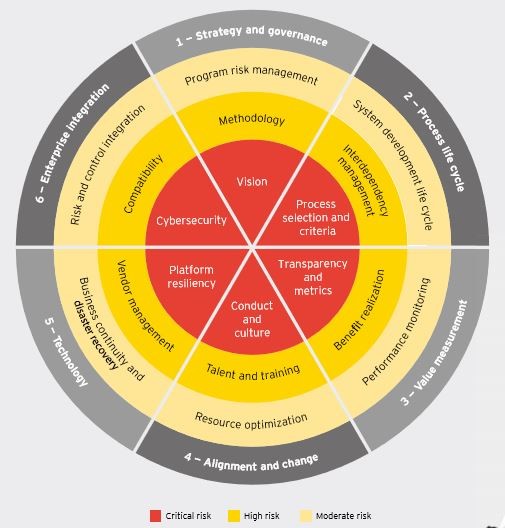
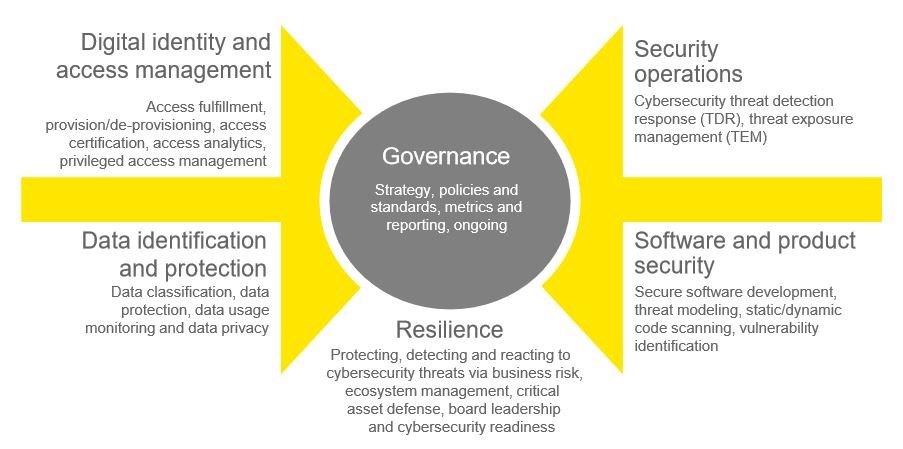
4. Best Practices to Secure RPA environment:
Never automate a broken process
- Ensure the process is stable and optimized before automation is applied using a bot
RPA should always sit with the Process owner
- Run by Business stakeholders with support from IT
- Grow in house RPA of a mixture of Operations and IT people
Involve GRC throughout the entire process
- RPA will impact the entire Internal Control environment along with the dynamic interaction across all 3 Lines of Defense
RPA is not a project. RPA is a journey
- Don’t be tempted of quick wins by deploying RPA in siloed units
- Use pilots to remove roadblocks and align RPA strategy to business objectives
- Multi-skill the robots
The success of RPA depends on an institutionalized Sponsor
- RPA needs an institutionalized Robotic Team led by a Sponsor- who initiates the idea of automation, underwrites resources and protects progress into business adoption
Bring IT, Risk and Information Security onboard early
- RPA deployment has an impact on Infra, Security, Business Continuity and Disaster Recovery.
- RPA must comply with governance and architecture policies.
Communicate, Communicate, Communicate!
- Engage a dedicated team of Change and Communication for awareness in the business of the benefits of automation
- Keep all stakeholders up to speed with the progress of the automation process
5. Definitions:
- STP: Straight Through Processing (STP) is a process that financial companies use to speed up their transaction processing time. The main point of STP is to allow companies to have the same information to be streamlined through a process across multiple points.
- BOT: A bot (short for robot) also known as web robots is a program that operates automated tasks over the Internet as an agent for a user or another program or simulates a human activity.
- IPE/IUC: Information produced by Entity (IPE)/Information used in a control (IUC) The effectiveness of the control is dependent upon the accuracy and completeness of the information. Identify and test the controls that address the accuracy and completeness of information used in relevant control.
For more Blogs Click here