Threat Hunting for Masquerading Windows Processes
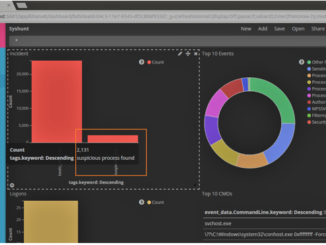
An important aspect of effective threat hunting is to understand what is normal in an environment. If a threat hunter is able to baseline the normal behaviour in a system [more]

An important aspect of effective threat hunting is to understand what is normal in an environment. If a threat hunter is able to baseline the normal behaviour in a system [more]
Copyright © 2024 | WordPress Theme by MH Themes