What is POODLE?
POODLE stands for Padding Oracle On Downgraded Legacy Encryption
Vulnerability CVE:
CVE-2014-3566
What is the attack?
The attack occurs when an attacker is able to downgrade the client to use SSLv3. By simulating a failure during the negotiation process, an attacker can force a browser and a server to renegotiate using an older protocol, right back down to SSLv3.
Attacker aims to capture the session cookie within a HTTPS tunnel through MITM. Attacker injects a piece of JavaScript and intercepts the outgoing messages and reorganizes them. This JavaScript tells the browser to repeatedly try to load an image from the Web application transmitting a session cookie. This image request will carry with it the session cookie and the JavaScript ensures that each of these requests is constructed in such a way as to ensure that one byte of the session cookie is placed in a particular place within each SSL message.
In this way, attacker will learn a single byte of the session cookie with every request and the complete session cookie can be decrypted to gain malicious access to the application.
How to check if I am vulnerable?
Visiting the below URL would confirm if the vulnerability exists.
https://dev.ssllabs.com/ssltest/viewMyClient.html
What is the fix?
- Disable SSLv3 support on the server.
- Use TLS_FALLBACK_SCSV, a mechanism that prevents attackers from forcing Web browsers to use SSL 3.0.For TLS clients:
TLS clients that use a downgrade dance to improve interoperability should include the value 0x56, 0x00 (TLS_FALLBACK_SCSV) in ClientHello.cipher_suites in any fallback handshakes. Thus, in case of a downgrade attack, clients would always fall back to the next lower version (if starting at TLS 1.2, try TLS 1.1 next, then TLS 1.0, then SSL 3.0) (With TLS_FALLBACK_SCSV, skipping a version also could entirely prevent a successful handshake if it happens to be the version that should be used with the server in question.)
For TLS servers:
In TLS servers, whenever an incoming connection includes 0x56, 0x00 (TLS_FALLBACK_SCSV) in ClientHello.cipher_suites, compare ClientHello.client_version to the highest protocol version supported by the server. If the server supports a version higher than the one indicated by the client, reject the connection with a fatal alert.
This use of TLS_FALLBACK_SCSV will ensure that SSL 3.0 is used only when a legacy implementation is involved and attackers can no longer force a protocol downgrade. (Attacks remain possible if bothparties allow SSL 3.0 but one of them is not updated to support TLS_FALLBACK_SCSV, provided that the client implements a downgrade dance down to SSL 3.0.) - Avoid potential phishing emails from attackers – to avoid going to an impersonated website.
How to fix this vulnerability on servers?
APACHE
- To disable SSLv3 on the Apache server, the following can be configured:
S S L P r o t o c o l A l l – S S L v 2 – S S L v 3 - This will ensure that TLSv1.0, TLSv1.1 and TLSv1.2 are supported and explicitly remove support for SSLv2 and SSLv3. Check the config and then restart Apache.
a p a c h e c t l c o n f i g t e s t
s u d o s e r v i c e a p a c h e 2 r e s t a r t
NGINX
- Disabling SSLv3 support on NginX is as follows :
s s l _ p r o t o c o l s T L S v 1 T L S v 1 . 1 T L S v 1 . 2 - Similar to the Apache config above, TLSv1.0+ would be supported and no SSL would be enabled. Check the config and restart :
s u d o n g i n x – t
s u d o s e r v i c e n g i n x r e s t a r t
IIS
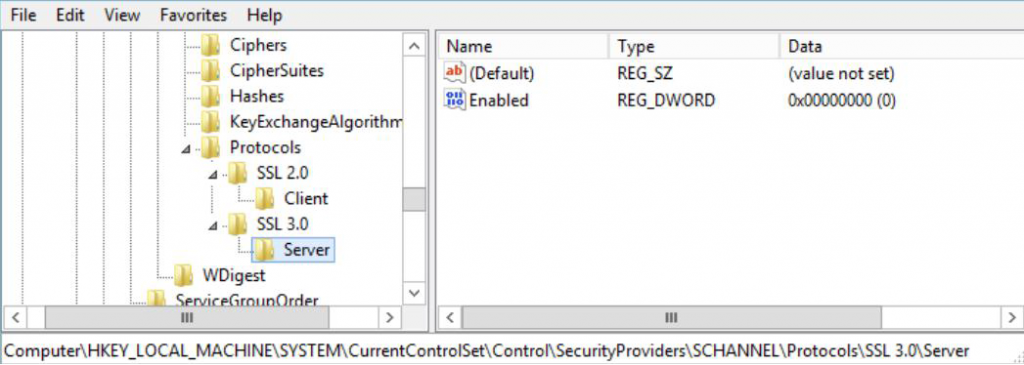
- Modify / create a registry DWORD value.
H K e y _ L o c a l _ M a c h i n e \ S y s t e m \ C u r r e n t C o n t r o l S e t \ C o n t r o l \ S e c u r i t y P r o v i d e r s \ S C H A N N E L \ P r o t o c o l s - Inside protocols, the S S L 2 . 0 key would be already present, so create S S L 3 . 0 alongside it if needed. Under that create a S e r v e r key and inside there a DWORD value called E n a b l e d with value 0 . Once that’s done reboot the server for the changes to take effect.
How to fix this vulnerability on browsers:
Firefox:
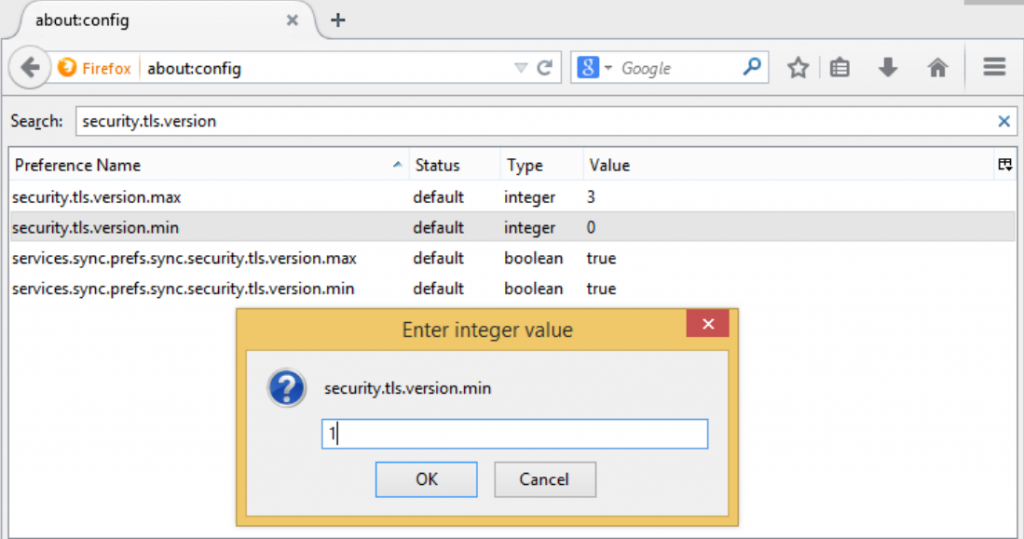
- Type a b o u t : c o n f i g into their address bar
- Type s e c u r i t y . t l s . v e r s i o n . m i n into the search box. This will bring up the setting that needs to be changed from 0 to 1.
- By changing the setting Firefox will be forced to only use TLSv1.0 or better, which is not vulnerable to POODLE.
CHROME:
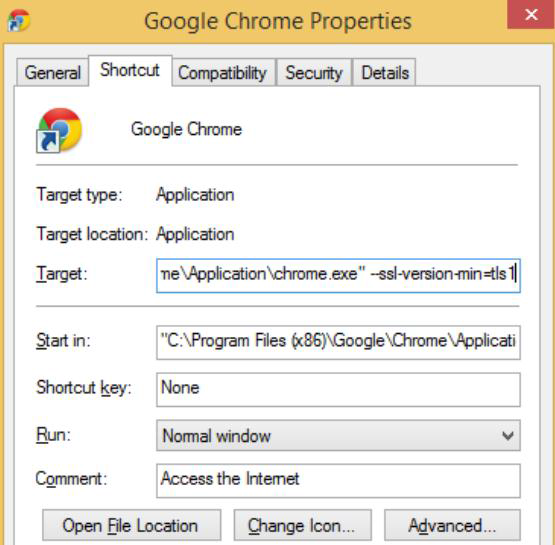
- Add the command line flag – – s s l – v e r s i o n – m i n = t l s
- In Windows, right click on the Chrome shortcut, hit Properties and add the command line flag
INTERNET EXPLORER:
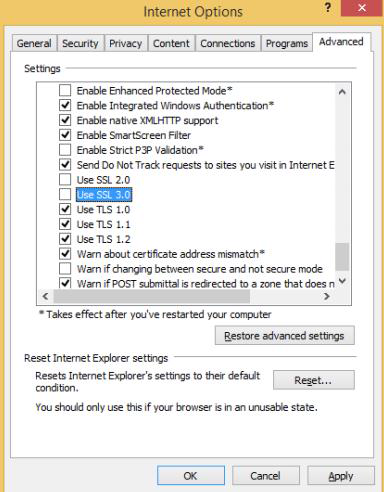
- Go to Settings, Internet Options and click on the Advanced tab.
- Uncheck the U s e S S L 3 . 0 checkbox
Shortcomings in the fix:
Systems using IE6 and Windows XP installations below SP3, will no longer be able to communicate with any site that does not use SSLv3.
Alex Rajan works as an Information Security Analyst at NII. He has carried out Vulnerability Assessments and Penetration Tests for Web Applications and Networks. He has good understanding of cloud application security. He has handled projects in Banking, Insurance and Trading sectors. He also provides training with Institute of Information Security (IIS) – the training arm of NII. He is an active member and a speaker at Nullcon (Mumbai Chapter).