Recently there has been a lot of news about a new SSL/TLS based attacks which was demonstrated in this year’s BlackHat conference. The attack was on SSL/TLS and was dubbed BREACH attack. The attack targeted sensitive data being transmitted in HTTP responses. In this article we will explore the BEAST attack as well as two other well known sophisticated attacks on SSL/TLS protocol such as CRIME and BREACH.
Browser Exploit Against SSL/TLS (BEAST) attack:
The BEAST is client side attack. As per SSL Pulse project monitoring SSL/TLS implementations, 75% of the world’s SSL enabled websites are vulnerable to BEAST attack.
The attack on SSL leverages a generic cryptographic attack called the ‘Chosen Plaintext attack’. The attack is effective only when block ciphers are used. When encrypting the plain text, the text is divided into blocks. Each block is first XOR’d with the previous cipher text and then encrypted with the chosen key. However, the very first block is XOR’d with a randomly chosen value called the initialization vector (IV).
Pre-requisites for BEAST attack to work:
- The SSL enabled web server must be running version of SSL 3.0 or lower or TLS 1.0.
- It must support Block ciphers CBC.
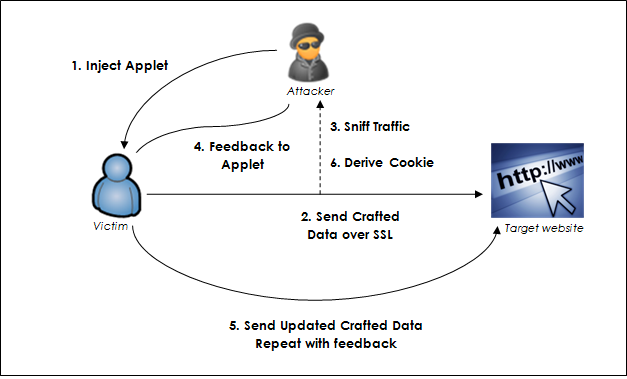
- The attacker must be able to mix his content with the SSL content.
- The attacker must implement a Man-in-the-middle (MITM) so that he can observe the SSL traffic. Although, he will not be able to decipher the content within.
- The attack only works on block ciphers such as AES, DES only. Stream ciphers are not affected by it.
Injecting content with SSL content can be done via:
- SSL VPN
- Java plug-in to bypass SOP.
- JavaScript to initiate connections to the target site with SSL enabled.
Working of the BEAST attack
Consider a connection between the victim and the server.
- The attacker observes the traffic and let’s say the attacker knows that the victim’s password is in the block x. i.e. the password is Tx, which represents the plaintext of the block x.
- The attacker can also know that the IV to be used to XOR the password is the cipher text from the previous encrypted block let’s say it is Cx-1 .The password will be XOR’d like thisCx-1 ⊕Tx
Here, Tx is the actual password text. This XOR’d information will be encrypted. This will then give the cipher text which we will call Cx which will be used as the IV for the next block. Let us call this IV as IV2. - The attacker now tries to the guess the password and checks if the password is correct by simply observing the encrypted traffic. The attacker guesses that the password may be P, which represents a password string.
- The attacker will also know that the next IV is IV2. This the attacker can get simply by observing the traffic. The attacker now injects a block with the following valueIV2⊕ Cx-1 ⊕ P
Here Cx-1 is the encrypted message of the block prior to the block containing the password. - The injected plain text is XOR’d with the IV2
The XOR function will look like this(IV2⊕ Cx-1 ⊕ P)⊕ IV2The two IV2 are XOR’d and cancel each other; giving out
Cx-1⊕P
If P=Tx then the attacker has successfully guessed the password. If not the attacker can simply repeat the process until the password has been guessed.
Mitigations for BEAST attack:
The BEAST attack can be prevented in the following ways:
- Using TLS 1.1 or TLS 1.2. (Strongly Recommended)
- If using a lower version of TLS or if the server is using SSL then use a stream cipher such as RC4.
The BEAST is truly an ingenious way to leverage the Chosen Plaintext attack to weaken the SSL/TLS protocol. In the next section we explore another attack called the CRIME.
Asif Balasinor has varied experience in the field of information security and digital forensics. He has carried out Vulnerability Assessments and Penetration Tests for Web Applications and Networks.
“The password will be XOR’d like this Cx-1 ⊕Tx
Here, Tx is the actual password text. This XOR’d information will be encrypted.”
Actually in CBC it’s the other way around. The plaintext will be encrypted and then XORed with the previous block’s ciphertext.
Sorry you were right. Disregard the previous message