Scenario:
One of our clients observed a suspicious behavior in a program and wanted us to analyze and identify if any malicious activities were being performed by the same. The program wasn’t detected by their anti-virus solution during ‘file access operations’. However, some unusual outbound network traffic triggered alerts from the network monitoring team.
| Filename | Size (in bytes) | File Type | Hash |
| pprtc.exe | 71,168 | PE (Win32) | (MD5)dda3b490cd01690e12b280e5bb935bce (SHA1)ca4175a0c526d1be74fd1b00668e0799e41f0e76 |
Table 1: Suspect File Details
Opening the file in Hex-editor, it was found that suspect file was ‘packed’ using UPX.UPX is a program often used by virus writers to bypass Anti-Virus protection by compression techniques. When the UPX program is used with any clean binaries, all original PE sections, i.e., text, data, rsrc etc., will get compressed. These compressed sections will be aligned under the name of UPX, UPX0 and UPX1, as you can see in Figure 1 below. UPX then adds an additional code with which it will decompress these sections before actual execution.
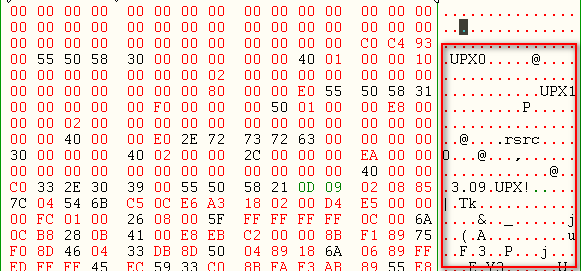
Unpacking such packed binaries is quite straight forward. We can use the packing program (UPX.exe in this case) to unpack the EXE as shown below:
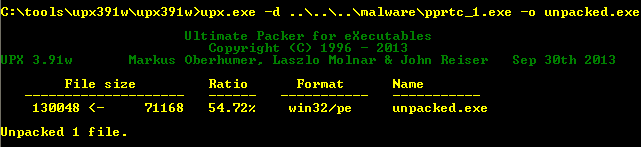
After unpacking, original/unpacked binary was found with hash value of fd818e8433a7804ba8a57cea50dcafff (MD5)
The initial phase of analysis was to identify the behavior of suspected file execution by setting up a sandbox with relevant tools. This is called ‘Dynamic Malware Analysis’. I shall try to explain the tools and setup required for dynamic analysis in a future a blog post.
During dynamic analysis we are mainly looking at the run-time execution of suspect file:
- Is it making any process calls?
- Are there any system file (read/write) operations being performed?
- Any registries being accessed?
- Is it making any remote network connection?
- If it is connecting to remote servers, is it transferring any information?
Analyzing Processes & I/O Operations
While inspecting the process calls, it was found that suspect program calls theWindows Service Host Process (svchost.exe), which is implemented where multiple services share one process for reducing load of system resources [1].
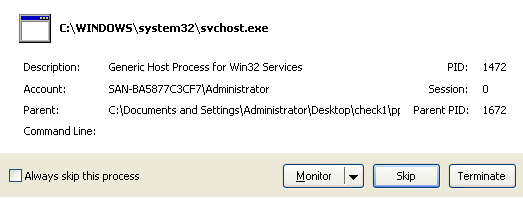
The file I/O operations were also analyzed and found that suspect program was accessing following files;
%USERPROFILE%\Application Data\Mozilla\Firefox\Profiles\iruggagh.default\webappsstore.sqlite
%USERPROFILE%\Local Settings\Temporary Internet Files
These files are the browser history data-stores for Firefox and Internet Explorer respectively.
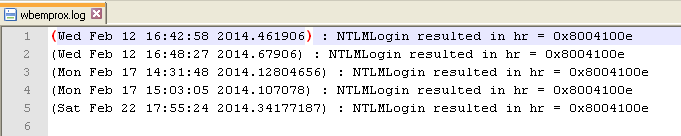
The Infected system created Windows Management Instrumentation (WMI) log file [2] during the execution of suspect binary.
%WINDIR%\system32\WBEM\Logs\wbemprox.log
This system file contains WMI proxy server information affecting to connectivity issues. As showen in the figure below, it was found that suspect program was trying to perform some privileged operations.
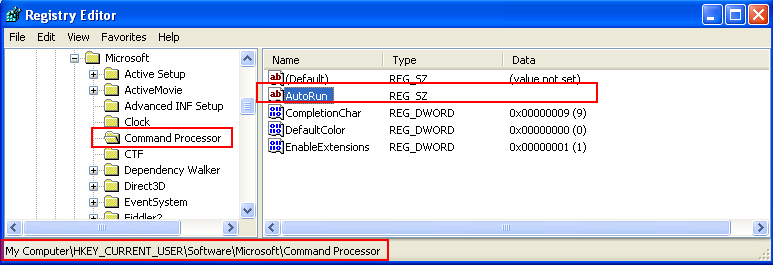
The suspect program was also performs certain registry operations. One of the interesting registry modifications noticed during analysis was an additional key value (i.e., null value) to registry entry of Windows command prompt HKCU\Software\Microsoft\Command Processer\AutoRun. This means the Windows command program will be non-functional as the AutoRun, i.e., startup parameter, was set to NULL.
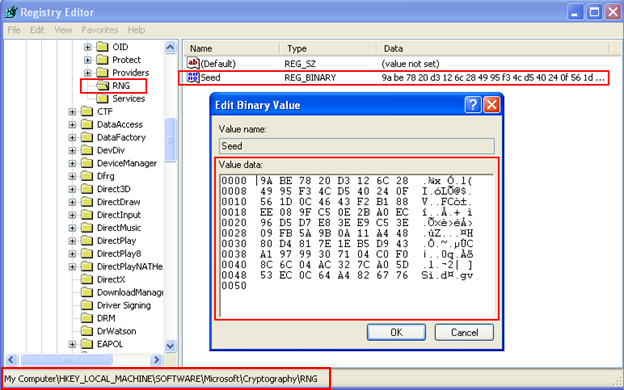
The suspect program also added a crypto seed into the registry. This means the program was possibly using anti-reversing techniques. We will see more details about this in static analysis.
Analyzing Network Operations
While analyzing the network communication during dynamic analysis, it was found that the suspect binary made HTTP requests to multiple domains. The network traffic was captured in a sandbox environment and you can download the raw PCAP file from here.
Calls to following domains were identified
- obofonaxy.nl
- aqaxiboqe.nl
- ducyqaxas.nl
- codudiref.nl
- fojavexuz.nl
- walaleqiw.nl
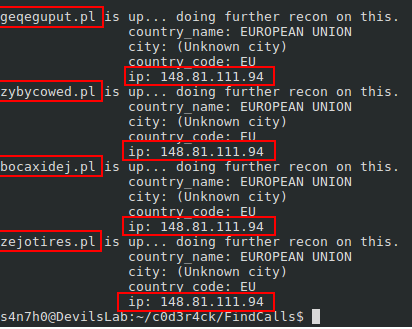
- geqeguput.pl
- zybycowed.pl
- zejotires.pl
- bocaxidej.pl
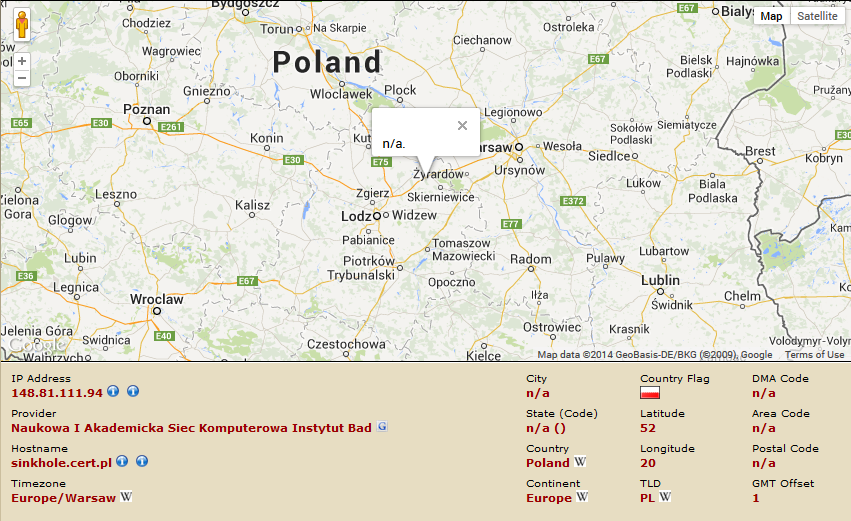
All the Netherland domains (.nl domains) were dead at the time of analysis. But all the Poland domains (.pl domains) resolved to the same IP address: 148.81.111.94
With a brief understanding of what the binary was trying to do on a victim’s machine, we now proceed to conduct a static analysis. We first need to identify any anti-reversing techniques used by the program.
Loading up the malware in a debugger (IDA Free 5.0) we manually step-into each instruction and try to identify if the isDebuggerPresent function is being called. This function is used by the binary to identify if any debugger is attached to the process.
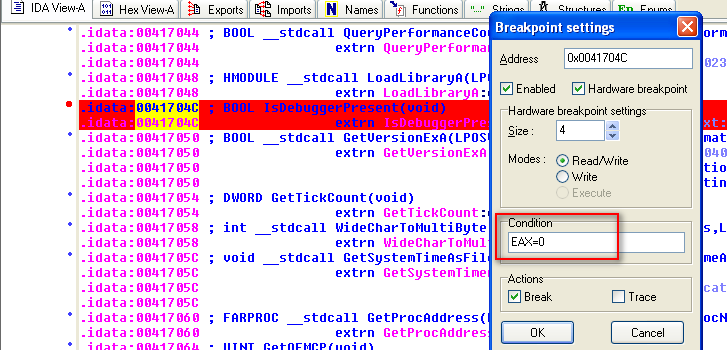
This anti-reversing protection can be easily bypassed. To do this, we setup a breakpoint with a user-defined condition – assign EAX to 0(so that each time when the function gets called, it should sets the value 0 in EAX).This needs to be done at all locations where a reference to the isDebuggerPresent function is made. As the condition always returns 0 and the malware binary then interprets this as debugger is not present.
The suspect binary was found to be using self-modifying routines which is a sophisticated technique used by malware authors to dynamically change the code during execution.
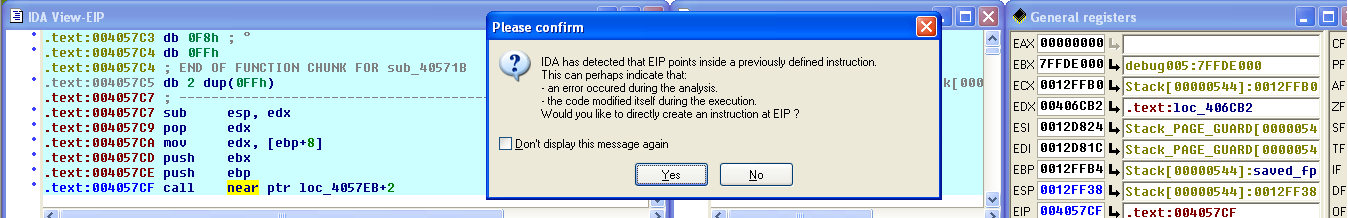
Self-modifying code makes a program appear different from it’s actual code. In this case, the suspect program was passing through a set of routines iteratively which changes the existing code during execution. In the screenshot below, we can see multiple calls to address spaces which are used by the self-modifying routines.
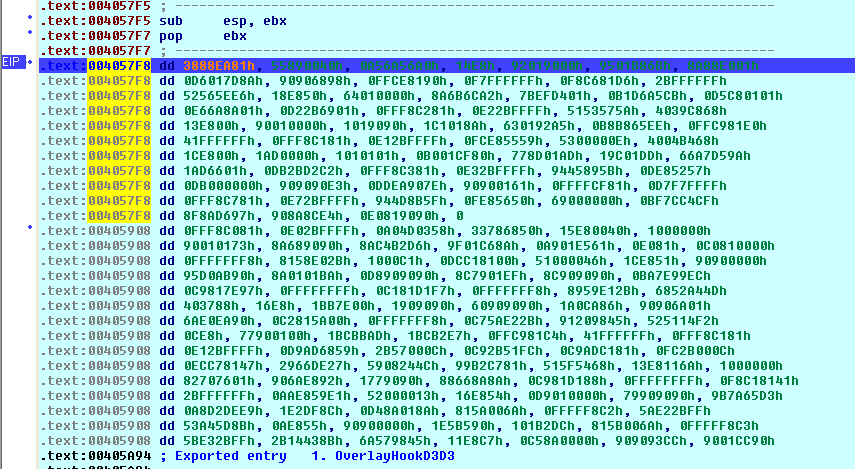
Overall, we can conclude that the suspect program was crafted by sophisticated writers with multiple anti-reversing techniques such as packers, debugger-detection, cryptographic techniques and self-modifying routines.
However, a previous analysis report available at VirusTotal displayed a lot of similarities to our suspect binary.
https://www.virustotal.com/en/ip-address/199.217.115.62/information/
Although the IP address mentioned in this analysis was not found in our network capture, the domain names and URL calls were found to be the same.
The suspected binary was scanned using VirusTotal API and the result as follows
| AV Name | Detection Result |
| MicroWorld-eScan | Gen:Variant.Kazy.213219 |
| McAfee | RDN/Generic.tfr!dn |
| K7AntiVirus | Trojan |
| K7GW | Trojan |
| TheHacker | Posible_Worm32 |
| Agnitum | Trojan.Droma!RnznSPio82Q |
| Symantec | WS.Reputation.1 |
| Norman | Moure.B |
| TrendMicro-HouseCall | TROJ_GEN.F0C2C0KH513 |
| Avast | Win32:Malware-gen |
| Kaspersky | Trojan.Win32.Droma.c |
| BitDefender | Gen:Variant.Kazy.213219 |
| NANO-Antivirus | Trojan.Win32.Droma.caesga |
| Emsisoft | Gen:Variant.Kazy.213219 (B) |
| Comodo | UnclassifiedMalware |
| F-Secure | Gen:Variant.Kazy.213219 |
| DrWeb | Trojan.KillProc.28071 |
| VIPRE | Trojan-Downloader.Win32.Moure.ba (v) |
| AntiVir | TR/Kazy.213219 |
| TrendMicro | TROJ_GEN.F0C2C0KH513 |
| McAfee-GW-Edition | RDN/Generic.tfr!dn |
| Sophos | Mal/Generic-S |
| Jiangmin | Backdoor/Androm.biz |
| Antiy-AVL | Trojan/Win32.Droma |
| AhnLab-V3 | Trojan/Win32.LockScreen |
| GData | Gen:Variant.Kazy.213219 |
| Commtouch | W32/Backdoor.IGGZ-7997 |
| VBA32 | BScope.Trojan.AET.8807 |
| ESET-NOD32 | Win32/TrojanDownloader.Moure.X |
| Ikarus | Trojan.Win32.Droma |
| Fortinet | W32/Krap.JI!tr |
| AVG | BackDoor.Generic17.ALQS |
References:
- Service Host : http://en.wikipedia.org/wiki/Svchost.exe
- WMI Service Log Files : http://msdn.microsoft.com/en-us/library/aa827355%28v=vs.85%29.aspx
- FindDomainCalls : https://github.com/c0d3r4ck/FindDomainCalls/
- Naukowa i Akademicka Sieć Komputerowa : http://en.wikipedia.org/wiki/Naukowa_i_Akademicka_Sie%C4%87_Komputerowa
Sanoop Thomas currently serves as Senior Consultant at Network Intelligence India Pvt. Ltd. He also works as Head Security Trainer at the training division – Institute of Information Security.
His work mainly focuses on conducting security training, consistently do security researches, incident detection and response, VAPT assessments for web application, networks, servers and mobile applications for NII’s premier clients.
He has consistently impressed clients with his ability to think out of the box, and creatively attack systems and applications.
He is well versed with the security standard such as OWASP, WASC, OSSTMM, ISO 27001, PCI DSS etc.
His technical abilities span a very wide range of technologies across networks, operating systems, databases, web servers, and applications; however his specialization is in scripting security tools(automating), reverse engineering & malware analysis, wireless and mobile security etc.
Great article! Looking forward to your next one about your toolkit.
Thanks for writing.
-Alex
Every weekend i used to pay a quick visit this site, as i wish for enjoyment, since
this this web site conations genuinely good funny stuff too.