![]() Overview:
Overview:
In this following test, I wanted to see whether I was able to view personal details of some other person who was not in my connection list on LinkedIn. By default, LinkedIn doesn’t allow you to view the contact details of the person who is not in your connections list. Let us dig deeper to find out whether it is really possible.
Technical Details:
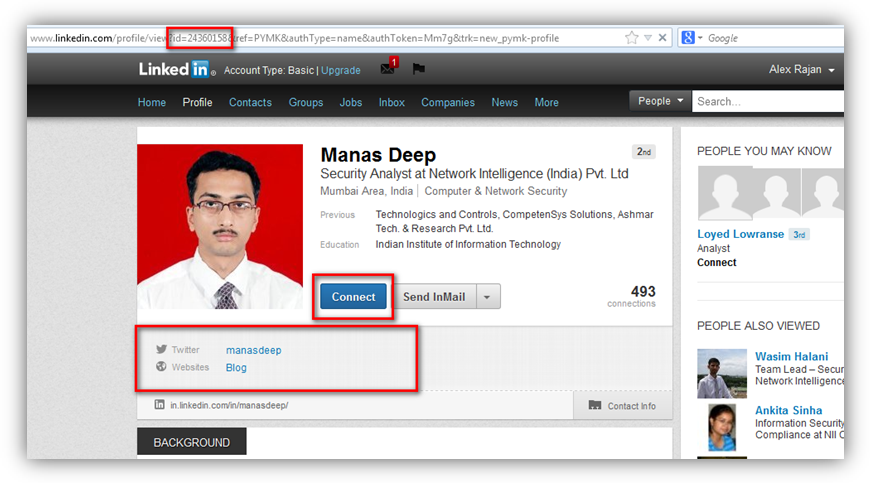
1) A user logs in to his LinkedIn Account and visits the profile of another user (in this case I chose target my connection Manas Deep) who was not in my connection list. From the below figure, it is evident that I was initially not able to view the contact details of my target connection Manas Deep.
2) Now, I visited my Connections tab and on clicking on my friend Abnawe Rajendra, I’m able to view the contact details of Rajendra Abnawe since he is in my Connections list.
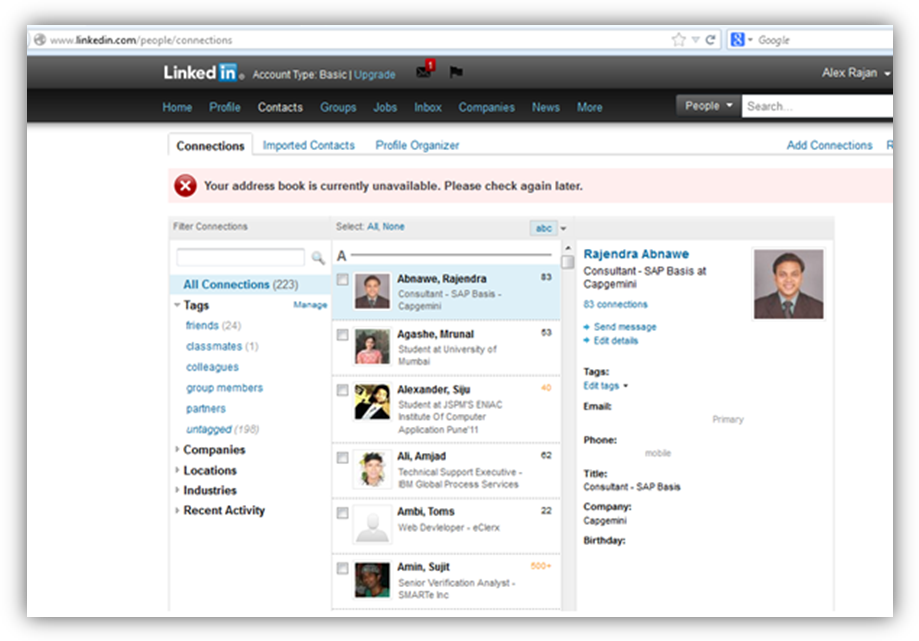
3) Observing the entire request by capturing it via Burp Suite proxy, I found out that when I clicked on a user connection, the browser actually sends a request to the application containing the member ID of his connection. Now, I modified the request by replacing the parameter of member id (retrieved from URL in Figure 1) with that of Manas Deep (who was not in my connections list) and sent it to the application.
![]()
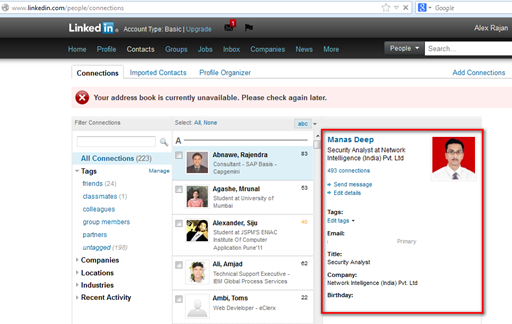
4) To my surprise, I was now able to see the complete contact details of Manas Deep. Here is the screenshot of the same as below.
5) Encouraged by this finding, I tried to leverage this attack by clicking on ‘Send Message’ to try sending a mail to Manas Deep. In ideal case, I should not be able to do that since by default the LinkedIn application restricts sending mails to users who are not in our connection list. The ‘Send message’ option is available through the ‘Compose Message’ module in the ‘Inbox’ tab.
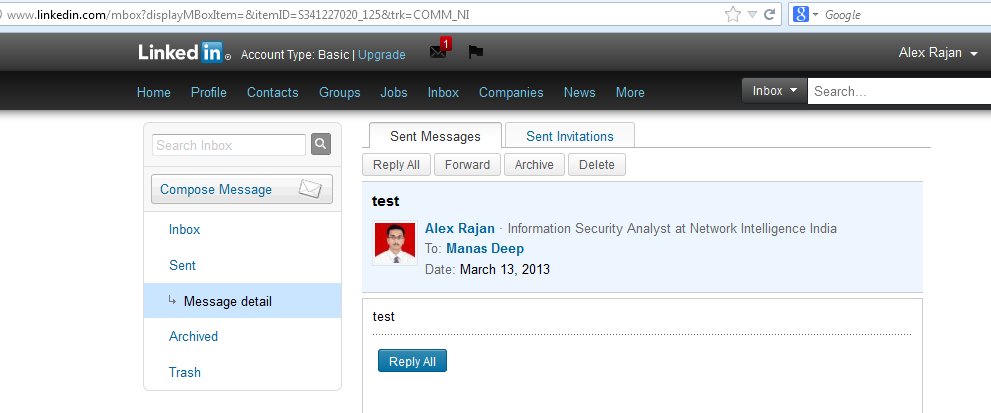
As evident from the screenshot above, I was able to successfully send the mail to Manas Deep even when he was not in my connection list. I did that by just replacing the Member ID with his Member ID.
Thus, in a similar fashion, an attacker can enumerate all its targeted Member IDs and collect their personal details. He can then leverage this to even send emails to all these users without adding them to the friends list.
Status:
Within 48 hrs of reporting this vulnerability on LinkedIn, their security team got in touch with me and addressed the vulnerability promptly. I appreciate the agility and quick action taken by of the LinkedIn team to protect the privacy of its clients.
Click here to view our previous finding on LinkedIn on Authentication bypass.
Alex Rajan works as an Information Security Analyst at NII. He has carried out Vulnerability Assessments and Penetration Tests for Web Applications and Networks. He has good understanding of cloud application security. He has handled projects in Banking, Insurance and Trading sectors. He also provides training with Institute of Information Security (IIS) – the training arm of NII. He is an active member and a speaker at Nullcon (Mumbai Chapter).
2
Nice article. I am writing a blog http://dfg-iiitdelhi.blogspot.in/
Very nice post. I just stumbled upon your weblog and wished to say that Ihave really enjoyed browsing your weblog posts.
After alll I wioll be subscribing for your rss feed and I’m hoping you write again very soon!